If you are reading this blog post via a 3rd party source it is very likely that many parts of it will not render correctly (usually, the interactive graphs). Please view the post on dogesec.com for the full interactive viewing experience.
tl;dr
We needed a way to link all of our threat intel research to detection rulesets in one place. Our solution; model Sigma Rules as STIX objects.
Overview
I would be willing to bet that for every hundred readers of this post, there will at least 10 different SIEM or XDR tools being used among you.
This is problematic because it adds a large amount of friction to the sharing detection content.
It is this pain that saw the birth of the Sigma project.
Sigma Rules were designed to be a single rule format that could be converted into other query languages, like Splunk’s query language, SPL, or Microsoft Sentinel’s KQL.
Sigma Rules themselves are written in YAML, making them easy to understand, modify, and sync with tools that understand the schema.
Unfortunately not many threat intelligence tools understand Sigma Rules (or any detection rules for that matter) which is a massive oversight because detection rules are threat intelligence, in my opinion.
To solve this problem we built sigma2stix that converts the Sigma Rules we write into STIX 2.1 objects (that are understood by most threat intelligence tools).
Ultimately sigma2stix allows us to keep all our intel, including detection rules, in a single intelligence graph.
Let me show you how sigma2stix does this…
STIX Modelling
Indicators
As I touched on in my post, Constructing STIX Indicator Patterns to Write Detection Rules, Indicator SDOs can used the pattern_type = sigma, and then post the entire Sigma Rule in the pattern property.
The Indicator SDO has other required properties that can be populated using the data inside the rule.
You can see how we model the creation of the Indicator object in sigma2stix here.
Here’s an example Sigma Rule, Suspicious Reg Add Open Command, modelled as STIX;
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--40404b4f-a318-5931-834e-911398ed34c8",
"created_by_ref": "identity--860f4c0f-8c26-5889-b39d-ce94368bc416",
"created": "2021-12-20T00:00:00.000Z",
"modified": "2022-12-25T00:00:00.000Z",
"name": "Suspicious Reg Add Open Command",
"description": "Threat actors performed dumping of SAM, SECURITY and SYSTEM registry hives using DelegateExecute key. The following false positives can result from this detection; Unknown",
"indicator_types": [
"malicious-activity",
"anomalous-activity"
],
"pattern": "{'title': 'Suspicious Reg Add Open Command', 'id': 'dd3ee8cc-f751-41c9-ba53-5a32ed47e563', 'status': 'test', 'description': 'Threat actors performed dumping of SAM, SECURITY and SYSTEM registry hives using DelegateExecute key', 'references': ['https://thedfirreport.com/2021/12/13/diavol-ransomware/'], 'author': 'frack113', 'date': '2021/12/20', 'modified': '2022/12/25', 'tags': ['attack.credential_access', 'attack.t1003'], 'logsource': {'category': 'process_creation', 'product': 'windows'}, 'detection': {'selection_1': {'CommandLine|contains|all': ['reg', 'add', 'hkcu\\\\software\\\\classes\\\\ms-settings\\\\shell\\\\open\\\\command', '/ve ', '/d']}, 'selection_2': {'CommandLine|contains|all': ['reg', 'add', 'hkcu\\\\software\\\\classes\\\\ms-settings\\\\shell\\\\open\\\\command', '/v', 'DelegateExecute']}, 'selection_3': {'CommandLine|contains|all': ['reg', 'delete', 'hkcu\\\\software\\\\classes\\\\ms-settings']}, 'condition': '1 of selection_*'}, 'falsepositives': ['Unknown'], 'level': 'medium'}",
"pattern_type": "sigma",
"valid_from": "2021-12-20T00:00:00Z",
"external_references": [
{
"source_name": "sigma-rule",
"url": "https://github.com/SigmaHQ/sigma/blob/r2024-04-29/rules/windows/process_creation/proc_creation_win_reg_open_command.yml",
"external_id": "rule"
},
{
"source_name": "sigma-rule",
"description": "dd3ee8cc-f751-41c9-ba53-5a32ed47e563",
"external_id": "id"
},
{
"source_name": "sigma-rule",
"description": "medium",
"external_id": "level"
},
{
"source_name": "sigma-rule",
"description": "test",
"external_id": "status"
},
{
"source_name": "sigma-rule",
"description": "frack113",
"external_id": "author"
},
{
"source_name": "mitre-attack",
"description": "tactic",
"external_id": "credential-access"
},
{
"source_name": "mitre-attack",
"url": "https://attack.mitre.org/techniques/T1003",
"external_id": "T1003"
},
{
"source_name": "sigma-rule",
"description": "https://thedfirreport.com/2021/12/13/diavol-ransomware/",
"external_id": "reference"
}
],
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"marking-definition--860f4c0f-8c26-5889-b39d-ce94368bc416"
]
}
MITRE ATT&CK Enterprise References
Inside Sigma Rules are tags with MITRE ATT&CK Enterprise IDs.
sigma2stix converts these into the labels inside the Indicator SDOs it creates for each rule. The labels look as follows;
"labels": [
"attack.T1055",
"attack.T1055.011",
"attack.privilege_escalation"
"attack.S0039"
]
The labels identifying ATT&CK IDs always start with attack. followed by the actual ATT&CK ID.
Using these IDs, it is possible to get the corresponding MITRE ATT&CK STIX Objects (retrieved from CTI Butler).
The workflow in sigma2stix works like so;
- convert the
attack.labelss inside the Indicator SDO into a valid ATT&CK ID (e.g.attack.T1055->T1055) - look up the ID using the CTI Butler API
GET /v1/attack-enterprise/objects/{attack_id}/- note, if a Tactic is reported
privilege_escalation, sigma2stix will use the name, not the ID, in a request, e.g.GET /v1/attack-enterprise/objects/?name=<TACTIC_NAME>
- note, if a Tactic is reported
- import the STIX object returned
- create a STIX relationship object between the ATT&CK object and the Indicator representing the Sigma Rule
Expanding these steps out into a real working example, here would be the flow if the Sigma Rule contained attack.T1055 in the labels property of the Indicator SDO.
Firstly, attack.T1055 is converted into the ATT&CK ID T1055.
A request for T1055 is made to the CTI Butler API;
curl -X 'GET' \
'https://api.ctibutler.com/v1/attack-enterprise/objects/T1055/' \
-H 'accept: application/json'
The following JSON object is returned, and imported by sigma2stix;
{
"page_size": 50,
"page_number": 1,
"page_results_count": 1,
"total_results_count": 1,
"objects": [
{
"created": "2017-05-31T21:30:47.843Z",
"created_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"description": "Adversaries may inject code into processes in order to evade process-based defenses as well as possibly elevate privileges. Process injection is a method of executing arbitrary code in the address space of a separate live process. Running code in the context of another process may allow access to the process's memory, system/network resources, and possibly elevated privileges. Execution via process injection may also evade detection from security products since the execution is masked under a legitimate process. \n\nThere are many different ways to inject code into a process, many of which abuse legitimate functionalities. These implementations exist for every major OS but are typically platform specific. \n\nMore sophisticated samples may perform multiple process injections to segment modules and further evade detection, utilizing named pipes or other inter-process communication (IPC) mechanisms as a communication channel. ",
"external_references": [
{
"source_name": "mitre-attack",
"url": "https://attack.mitre.org/techniques/T1055",
"external_id": "T1055"
},
{
"source_name": "GNU Acct",
"description": "GNU. (2010, February 5). The GNU Accounting Utilities. Retrieved December 20, 2017.",
"url": "https://www.gnu.org/software/acct/"
},
{
"source_name": "Elastic Process Injection July 2017",
"description": "Hosseini, A. (2017, July 18). Ten Process Injection Techniques: A Technical Survey Of Common And Trending Process Injection Techniques. Retrieved December 7, 2017.",
"url": "https://www.endgame.com/blog/technical-blog/ten-process-injection-techniques-technical-survey-common-and-trending-process"
},
{
"source_name": "RHEL auditd",
"description": "Jahoda, M. et al.. (2017, March 14). redhat Security Guide - Chapter 7 - System Auditing. Retrieved December 20, 2017.",
"url": "https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/security_guide/chap-system_auditing"
},
{
"source_name": "ArtOfMemoryForensics",
"description": "Ligh, M.H. et al.. (2014, July). The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory. Retrieved December 20, 2017."
},
{
"source_name": "Microsoft Sysmon v6 May 2017",
"description": "Russinovich, M. & Garnier, T. (2017, May 22). Sysmon v6.20. Retrieved December 13, 2017.",
"url": "https://docs.microsoft.com/sysinternals/downloads/sysmon"
},
{
"source_name": "Chokepoint preload rootkits",
"description": "stderr. (2014, February 14). Detecting Userland Preload Rootkits. Retrieved December 20, 2017.",
"url": "http://www.chokepoint.net/2014/02/detecting-userland-preload-rootkits.html"
}
],
"id": "attack-pattern--43e7dc91-05b2-474c-b9ac-2ed4fe101f4d",
"kill_chain_phases": [
{
"kill_chain_name": "mitre-attack",
"phase_name": "defense-evasion"
},
{
"kill_chain_name": "mitre-attack",
"phase_name": "privilege-escalation"
}
],
"modified": "2023-05-09T14:00:00.188Z",
"name": "Process Injection",
"object_marking_refs": [
"marking-definition--fa42a846-8d90-4e51-bc29-71d5b4802168"
],
"revoked": false,
"spec_version": "2.1",
"type": "attack-pattern",
"x_mitre_attack_spec_version": "2.1.0",
"x_mitre_contributors": [
"Anastasios Pingios",
"Christiaan Beek, @ChristiaanBeek",
"Ryan Becwar"
],
"x_mitre_data_sources": [
"Process: Process Access",
"Process: Process Modification",
"File: File Modification",
"Process: Process Metadata",
"File: File Metadata",
"Process: OS API Execution",
"Module: Module Load"
],
"x_mitre_defense_bypassed": [
"Application control",
"Anti-virus"
],
"x_mitre_deprecated": false,
"x_mitre_detection": "Monitoring Windows API calls indicative of the various types of code injection may generate a significant amount of data and may not be directly useful for defense unless collected under specific circumstances for known bad sequences of calls, since benign use of API functions may be common and difficult to distinguish from malicious behavior. Windows API calls such as <code>CreateRemoteThread</code>, <code>SuspendThread</code>/<code>SetThreadContext</code>/<code>ResumeThread</code>, <code>QueueUserAPC</code>/<code>NtQueueApcThread</code>, and those that can be used to modify memory within another process, such as <code>VirtualAllocEx</code>/<code>WriteProcessMemory</code>, may be used for this technique.(Citation: Elastic Process Injection July 2017) \n\nMonitor DLL/PE file events, specifically creation of these binary files as well as the loading of DLLs into processes. Look for DLLs that are not recognized or not normally loaded into a process. \n\nMonitoring for Linux specific calls such as the ptrace system call should not generate large amounts of data due to their specialized nature, and can be a very effective method to detect some of the common process injection methods.(Citation: ArtOfMemoryForensics) (Citation: GNU Acct) (Citation: RHEL auditd) (Citation: Chokepoint preload rootkits) \n\nMonitor for named pipe creation and connection events (Event IDs 17 and 18) for possible indicators of infected processes with external modules.(Citation: Microsoft Sysmon v6 May 2017) \n\nAnalyze process behavior to determine if a process is performing actions it usually does not, such as opening network connections, reading files, or other suspicious actions that could relate to post-compromise behavior. ",
"x_mitre_domains": [
"enterprise-attack"
],
"x_mitre_is_subtechnique": false,
"x_mitre_modified_by_ref": "identity--c78cb6e5-0c4b-4611-8297-d1b8b55e40b5",
"x_mitre_platforms": [
"Linux",
"macOS",
"Windows"
],
"x_mitre_version": "1.3"
}
]
}
And finally, this ATT&CK object is linked back to the Sigma Rule Indicator object. The relationship mapping to produce this link is shown here.
Here is an example of what it could look like for reference here;
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--b9d04d92-1143-5a58-9ffd-79eb91531246",
"created_by_ref": "identity--860f4c0f-8c26-5889-b39d-ce94368bc416",
"created": "2023-10-20T00:00:00.000Z",
"modified": "2023-10-20T00:00:00.000Z",
"relationship_type": "detects",
"description": "Example rule detects T1055",
"source_ref": "indicator--b68e4492-049a-4306-b5ae-5ca162eb1cb6",
"target_ref": "attack-pattern--43e7dc91-05b2-474c-b9ac-2ed4fe101f4d",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"marking-definition--860f4c0f-8c26-5889-b39d-ce94368bc416"
]
}
CVE references
Similar to ATT&CK references, CVEs are also reported in Indicator SDOs under the labels property (taken from the Sigma Rules tags property);
"labels": [
"cve.2021.44228"
]
The labels identifying CVE IDs always start with cve. followed by the actual CVE ID.
Our CVE STIX catalogue is managed by Vulmatch, but the lookup flow follows the same pattern as ATT&CK IDs;
- convert the
cve.labelss inside the Indicator SDO into a valid CVE ID (e.g.cve.2021.44228->CVE-2021-44228) - look it up using a request to the Vulmatch API
GET /v1/cve/objects/{cve_id}/ - import the STIX object returned
- create a STIX relationship object between the CVE object and the Indicator representing the Sigma Rule
Again, here’s a real example of that workflow…
cve.2021.44228 becomes CVE-2021-44228 which is then used in the Vulmatch API lookup;
curl -X 'GET' \
'https://api.vulmatch.com/v1/cve/objects/CVE-2021-44228/' \
-H 'accept: application/json'
Which returns the STIX representation of the CVE that is imported by sigma2stix;
{
"page_size": 50,
"page_number": 1,
"page_results_count": 1,
"total_results_count": 1,
"objects": [
{
"created": "2021-12-10T10:15:09.143Z",
"created_by_ref": "identity--562918ee-d5da-5579-b6a1-fae50cc6bad3",
"description": "Apache Log4j2 2.0-beta9 through 2.15.0 (excluding security releases 2.12.2, 2.12.3, and 2.3.1) JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default. From version 2.16.0 (along with 2.12.2, 2.12.3, and 2.3.1), this functionality has been completely removed. Note that this vulnerability is specific to log4j-core and does not affect log4net, log4cxx, or other Apache Logging Services projects.",
"extensions": {
"extension-definition--2c5c13af-ee92-5246-9ba7-0b958f8cd34a": {
"extension_type": "toplevel-property-extension"
}
},
"external_references": [
{
"source_name": "cve",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2021-44228",
"external_id": "CVE-2021-44228"
},
{
"source_name": "cwe",
"url": "https://cwe.mitre.org/data/definitions/CWE-20.html",
"external_id": "CWE-20"
},
{
"source_name": "cwe",
"url": "https://cwe.mitre.org/data/definitions/CWE-917.html",
"external_id": "CWE-917"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165225/Apache-Log4j2-2.14.1-Remote-Code-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165260/VMware-Security-Advisory-2021-0028.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165261/Apache-Log4j2-2.14.1-Information-Disclosure.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165270/Apache-Log4j2-2.14.1-Remote-Code-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165281/Log4j2-Log4Shell-Regexes.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165282/Log4j-Payload-Generator.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165306/L4sh-Log4j-Remote-Code-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165307/Log4j-Remote-Code-Execution-Word-Bypassing.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165311/log4j-scan-Extensive-Scanner.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165371/VMware-Security-Advisory-2021-0028.4.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165532/Log4Shell-HTTP-Header-Injection.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165642/VMware-vCenter-Server-Unauthenticated-Log4Shell-JNDI-Injection-Remote-Code-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/165673/UniFi-Network-Application-Unauthenticated-Log4Shell-Remote-Code-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/167794/Open-Xchange-App-Suite-7.10.x-Cross-Site-Scripting-Command-Injection.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/167917/MobileIron-Log4Shell-Remote-Command-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,VDB Entry",
"url": "http://packetstormsecurity.com/files/171626/AD-Manager-Plus-7122-Remote-Code-Execution.html"
},
{
"source_name": "[email protected]",
"description": "Exploit,Mailing List,Third Party Advisory",
"url": "http://seclists.org/fulldisclosure/2022/Dec/2"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://seclists.org/fulldisclosure/2022/Jul/11"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://seclists.org/fulldisclosure/2022/Mar/23"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Mitigation,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/10/1"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Mitigation,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/10/2"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/10/3"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/13/1"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/13/2"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/14/4"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "http://www.openwall.com/lists/oss-security/2021/12/15/3"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-397453.pdf"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-479842.pdf"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-661247.pdf"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-714170.pdf"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://github.com/cisagov/log4j-affected-db"
},
{
"source_name": "[email protected]",
"description": "Broken Link,Product,US Government Resource",
"url": "https://github.com/cisagov/log4j-affected-db/blob/develop/SOFTWARE-LIST.md"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory",
"url": "https://github.com/nu11secur1ty/CVE-mitre/tree/main/CVE-2021-44228"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00007.html"
},
{
"source_name": "[email protected]",
"description": "Release Notes",
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/M5CSVUNV4HWZZXGOKNSK6L7RPM7BOKIB/"
},
{
"source_name": "[email protected]",
"description": "Release Notes",
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/VU57UJDCFIASIO35GC55JMKSRXJMCDFM/"
},
{
"source_name": "[email protected]",
"description": "Release Notes,Vendor Advisory",
"url": "https://logging.apache.org/log4j/2.x/security.html"
},
{
"source_name": "[email protected]",
"description": "Patch,Third Party Advisory,Vendor Advisory",
"url": "https://msrc-blog.microsoft.com/2021/12/11/microsofts-response-to-cve-2021-44228-apache-log4j2/"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0032"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://security.netapp.com/advisory/ntap-20211210-0007/"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://support.apple.com/kb/HT213189"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-apache-log4j-qRuKNEbd"
},
{
"source_name": "[email protected]",
"description": "Broken Link,Exploit,Third Party Advisory",
"url": "https://twitter.com/kurtseifried/status/1469345530182455296"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://www.bentley.com/en/common-vulnerability-exposure/be-2022-0001"
},
{
"source_name": "[email protected]",
"description": "Mailing List,Third Party Advisory",
"url": "https://www.debian.org/security/2021/dsa-5020"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00646.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory,US Government Resource",
"url": "https://www.kb.cert.org/vuls/id/930724"
},
{
"source_name": "[email protected]",
"description": "Exploit,Third Party Advisory",
"url": "https://www.nu11secur1ty.com/2021/12/cve-2021-44228.html"
},
{
"source_name": "[email protected]",
"description": "Third Party Advisory",
"url": "https://www.oracle.com/security-alerts/alert-cve-2021-44228.html"
},
{
"source_name": "[email protected]",
"description": "Patch,Third Party Advisory",
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source_name": "[email protected]",
"description": "Patch,Third Party Advisory",
"url": "https://www.oracle.com/security-alerts/cpujan2022.html"
},
{
"source_name": "vulnStatus",
"description": "Analyzed"
},
{
"source_name": "sourceIdentifier",
"description": "[email protected]"
}
],
"id": "vulnerability--e8074409-1ebc-589f-9952-2c21732ca3e8",
"modified": "2024-07-24T17:08:24.167Z",
"name": "CVE-2021-44228",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"marking-definition--562918ee-d5da-5579-b6a1-fae50cc6bad3"
],
"spec_version": "2.1",
"type": "vulnerability",
"x_cvss": {
"v2_0": {
"base_score": 9.3,
"base_severity": "HIGH",
"exploitability_score": 8.6,
"impact_score": 10,
"source": "[email protected]",
"type": "Primary",
"vector_string": "AV:N/AC:M/Au:N/C:C/I:C/A:C"
},
"v3_1": {
"base_score": 10,
"base_severity": "CRITICAL",
"exploitability_score": 3.9,
"impact_score": 6,
"source": "[email protected]",
"type": "Primary",
"vector_string": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H"
}
}
}
]
}
And finally, the SRO linking the Sigma Rule Indicator and CVE is created, for example,
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--dfb97266-8b34-5fa5-8d0a-15081d71ed76",
"created_by_ref": "identity--860f4c0f-8c26-5889-b39d-ce94368bc416",
"created": "2023-10-20T00:00:00.000Z",
"modified": "2023-10-20T00:00:00.000Z",
"relationship_type": "detects",
"description": "Example rule detects CVE-2021-44228",
"source_ref": "indicator--b68e4492-049a-4306-b5ae-5ca162eb1cb6",
"target_ref": "vulnerability--e8074409-1ebc-589f-9952-2c21732ca3e8",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"marking-definition--860f4c0f-8c26-5889-b39d-ce94368bc416"
]
}
Putting it all together
I appreciate the above is fairly detailed. Let me show you how this all works using an example rule;
title: DEMO! Exploitation Indicators Of CVE-2022-21722
id: 2ece8816-b7a0-4d9b-b0e8-ae7ad18bc02b
status: experimental
description: THIS RULE IS A DEMO. DO NOT USE. IT DOES NOT DETECT CVE-2022-21722
references:
- https://example.com/reference1
- https://example.com/reference2
author: DOGESEC Demos
date: 2023/10/20
tags:
- attack.privilege_escalation
- attack.initial_access
- attack.t1114
- detection.emerging_threats
- cve.2022.21722
logsource:
product: cisco
service: syslog
definition: 'Requirements: Cisco IOS XE system logs needs to be configured and ingested'
detection:
keyword_event:
- '%WEBUI-6-INSTALL_OPERATION_INFO:'
- '%SYS-5-CONFIG_P:'
- '%SEC_LOGIN-5-WEBLOGIN_SUCCESS:'
keyword_user:
- 'cisco_tac_admin'
- 'cisco_support'
- 'cisco_sys_manager'
condition: keyword_event and keyword_user
falsepositives:
- Rare false positives might occur if there are valid users named "cisco_tac_admin" or "cisco_support", which are not created by default or CISCO representatives
level: high
Running
python3 sigma2stix.py \
--mode sigmayaml \
--file tests/demo_rule.yml
Produces the following bundle;
…which you can import into your threat intelligence platform. Here is an example using OpenCTI.
Import > Upload > Select your bundle.
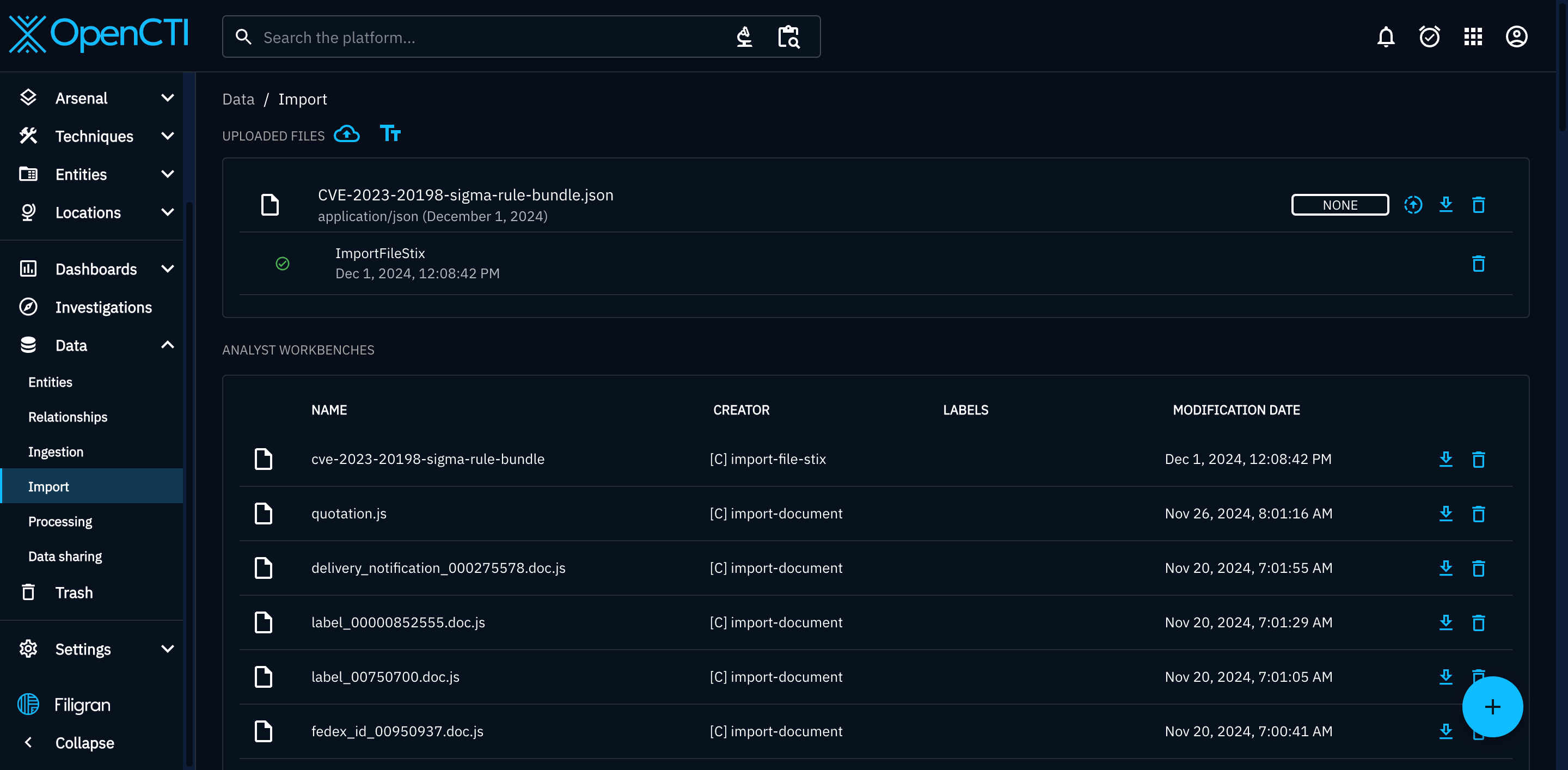
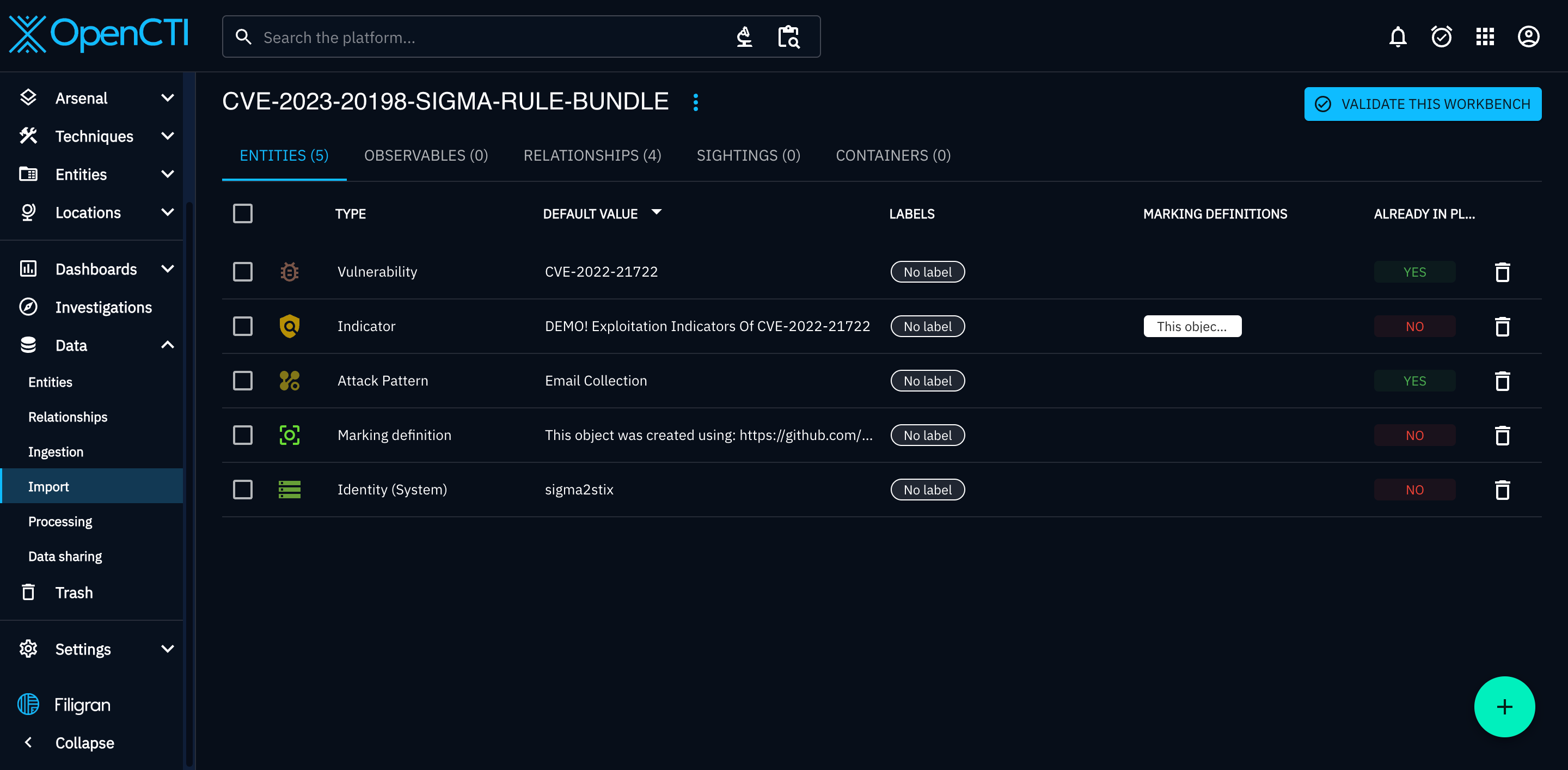
For us, this then slots into our wider intelligence graph. For example, all intelligence linked to CVE-2022-21722 (or whatever else we want to pivot on) could be loaded onto the graph.
If you’re looking to get started quickly, you can get sigma2stix to convert the entirety of the public Sigma Rules repository into STIX objects to load into your threat intelligence platform using the following command;
python3 sigma2stix.py \
--mode sigmahq \
--sigma_version_tag r2024-11-10
Here I use the latest version of the ruleset r2024-11-10.
Vulmatch
Straightforward vulnerability management. Know when software you use is vulnerable, how it is being exploited, and how to detect an attack.

SIEM Rules
Your detection engineering AI assistant. Turn cyber threat intelligence research into highly-tuned detection rules.

CTI Butler
One API. Much CTI. CTI Butler is the API used by the world's leading cyber-security companies.
Discuss this post
Head on over to the dogesec community to discuss this post.

Never miss an update
Sign up to receive new articles in your inbox as they published.
