Blog
The dogesec blog
-
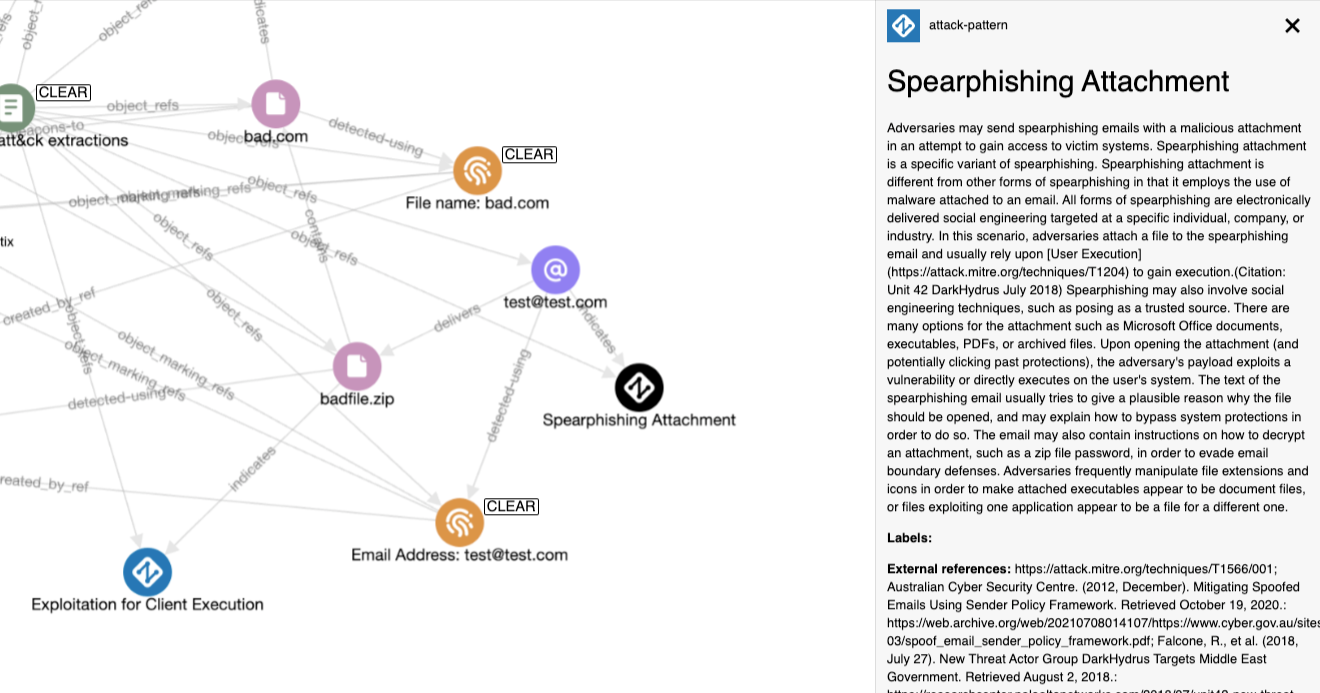
txt2stix: A Quick Start Guide to the New Features
TUTORIAL February 17, 2025
If you're a cyber threat intelligence analyst you probably use txt2stix, but do you know everything it's currently capable of? -
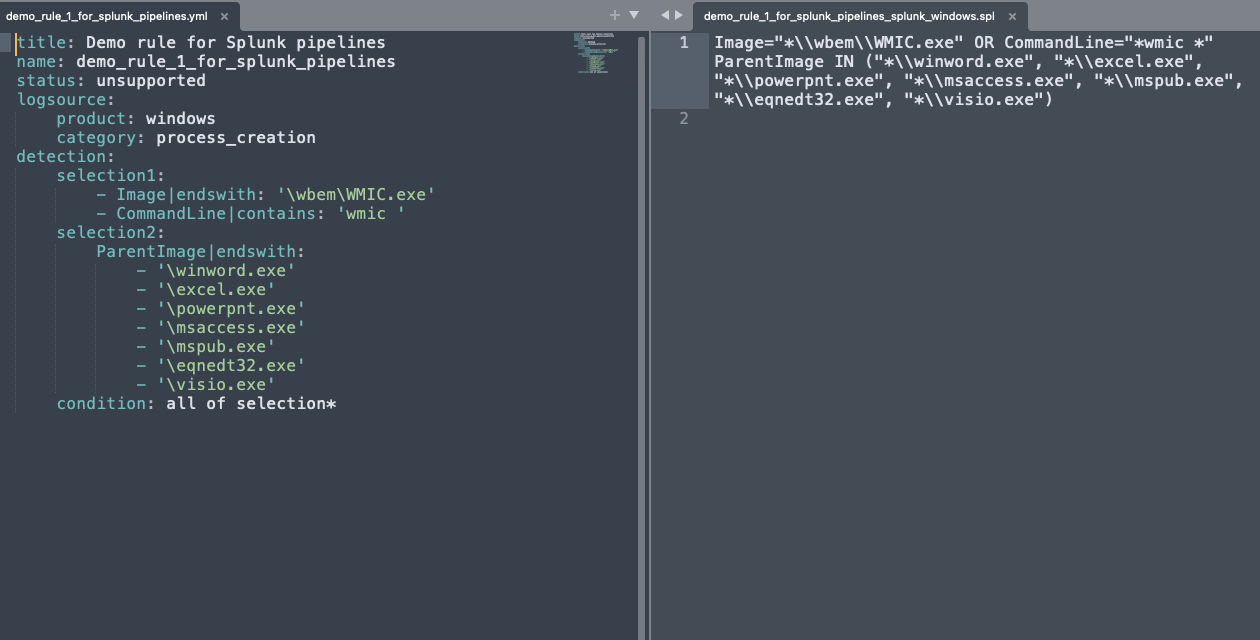
An Introduction pySigma: Converting Sigma Rules to Work with Your SIEM
TUTORIAL February 10, 2025
Learn how to seamlessly convert Sigma Rules into queries for your SIEM. Follow along with real examples. -
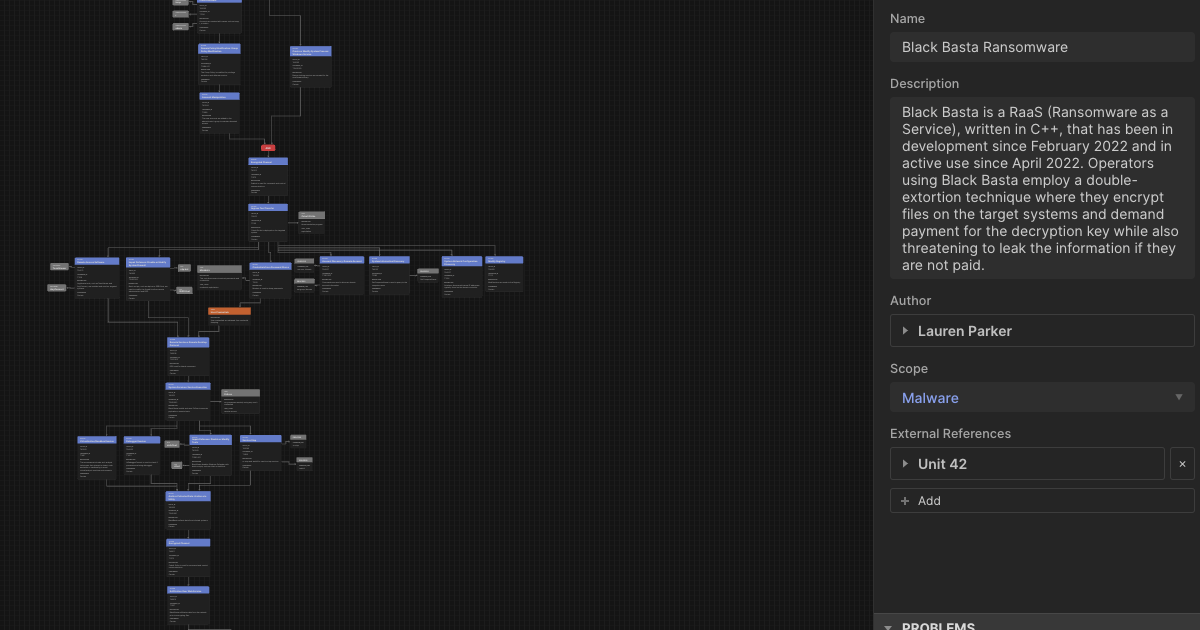
Beyond the ATT&CK Matrix: How to Build Dynamic Attack Flows with STIX
TUTORIAL February 03, 2025
MITRE ATT&CK techniques are useful, but they don’t capture the sequence of an attack. Enter Attack Flows. -
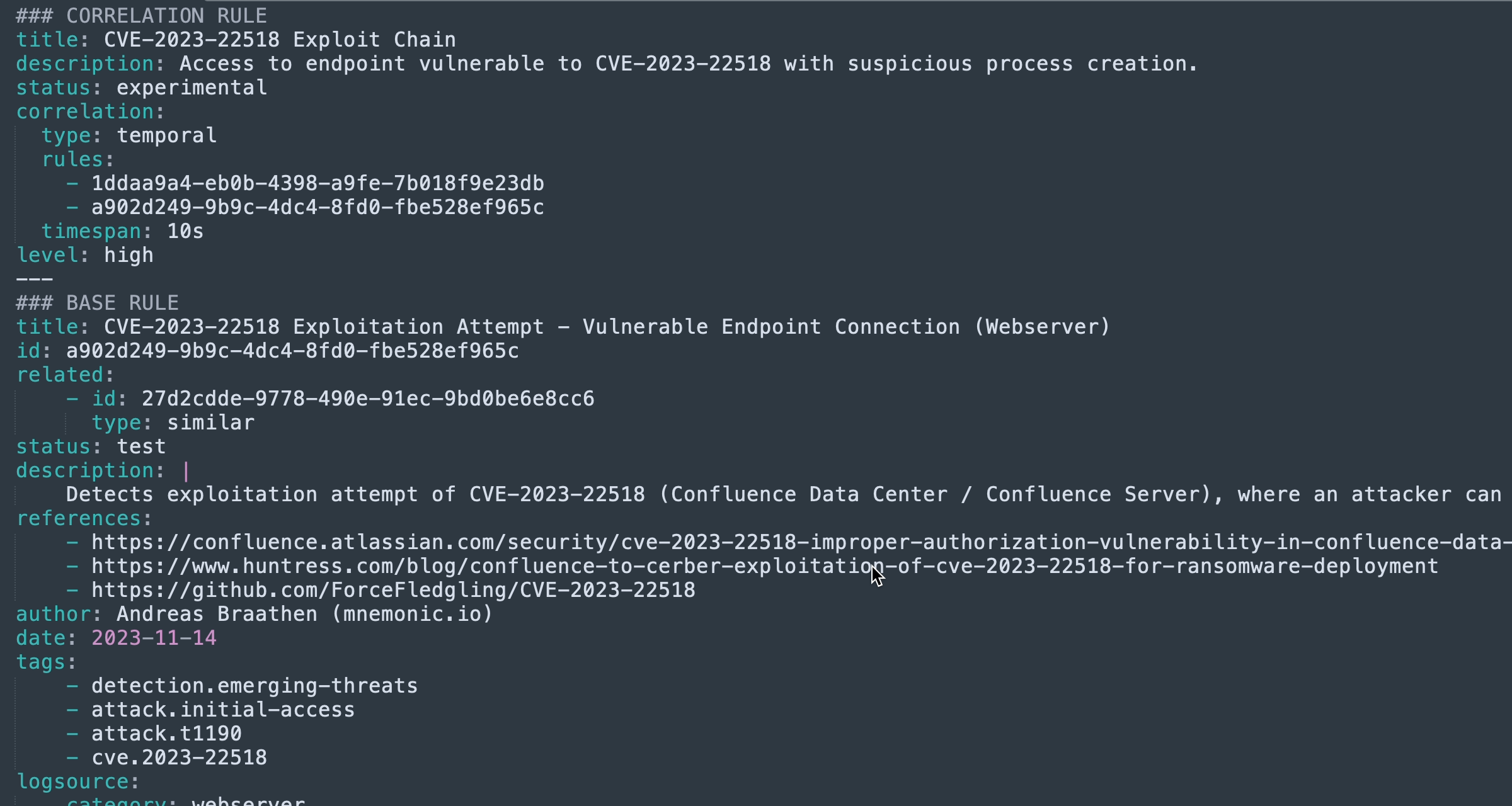
Writing Advanced Sigma Detection Rules: Using Correlation Rules
TUTORIAL January 27, 2025
Correlation Rules allow you to detect threats by linking multiple events together based on a meaningful relationship. -
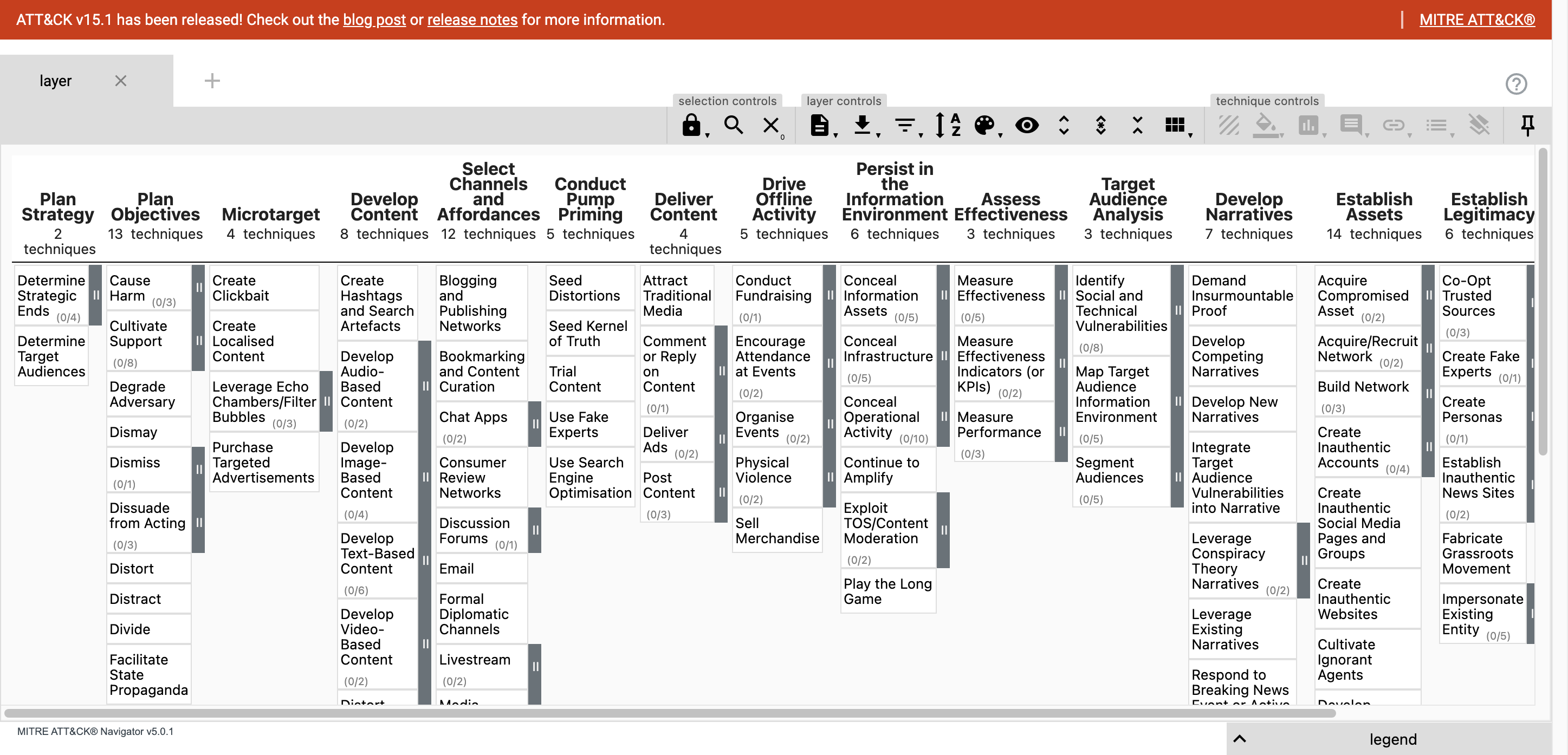
Getting Started with the MITRE ATT&CK Navigator
TUTORIAL January 13, 2025
The MITRE ATT&CK Navigator is a very useful tool to explore the MITRE ATT&CK (and other similar frameworks). In this post I take a look what you can do with Navigator and how it works under the hood so that you can use it to model your own ATT&CK-like frameworks. -
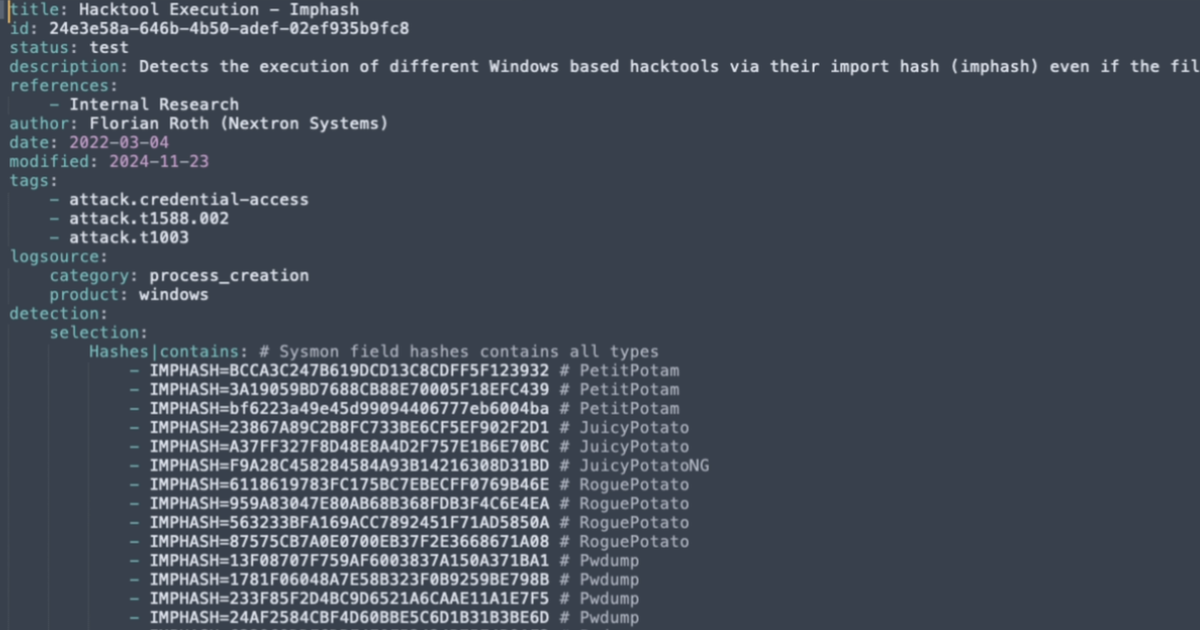
Writing Effective Sigma Detection Rules: A Guide for Novice Detection Engineers
TUTORIAL September 23, 2024
Sigma Rules are becoming more widely adopted as the standard detection language. Learning how to write them is not difficult. Let me show you. -
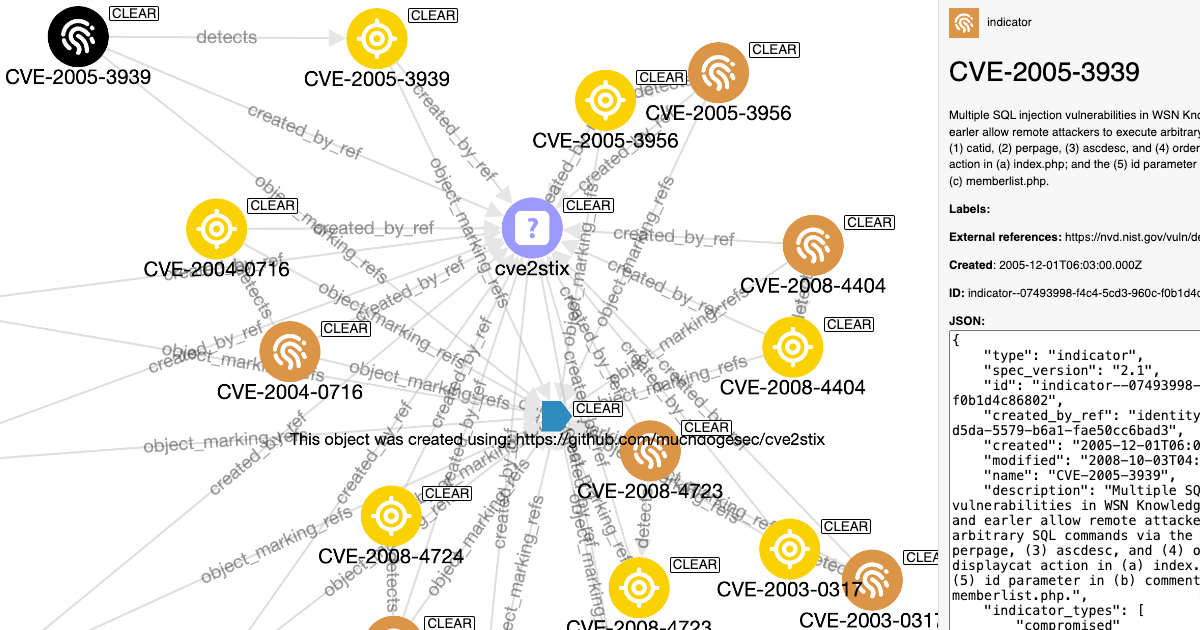
Using STIX Objects to Make Vulnerability Prioritisation Easy (and Free)
TUTORIAL September 02, 2024
Follow along as I show you how to store 200,000 CVEs as STIX objects, then use CVSS, EPSS, CISA KEV and CPE data to search and filter them. -
Writing Detection Rules to Identify if Products in my Stack are Vulnerable
TUTORIAL August 12, 2024
Developing on last weeks post, I show you how to construct STIX Patterns to automatically flag which products are affected by published CVEs. -
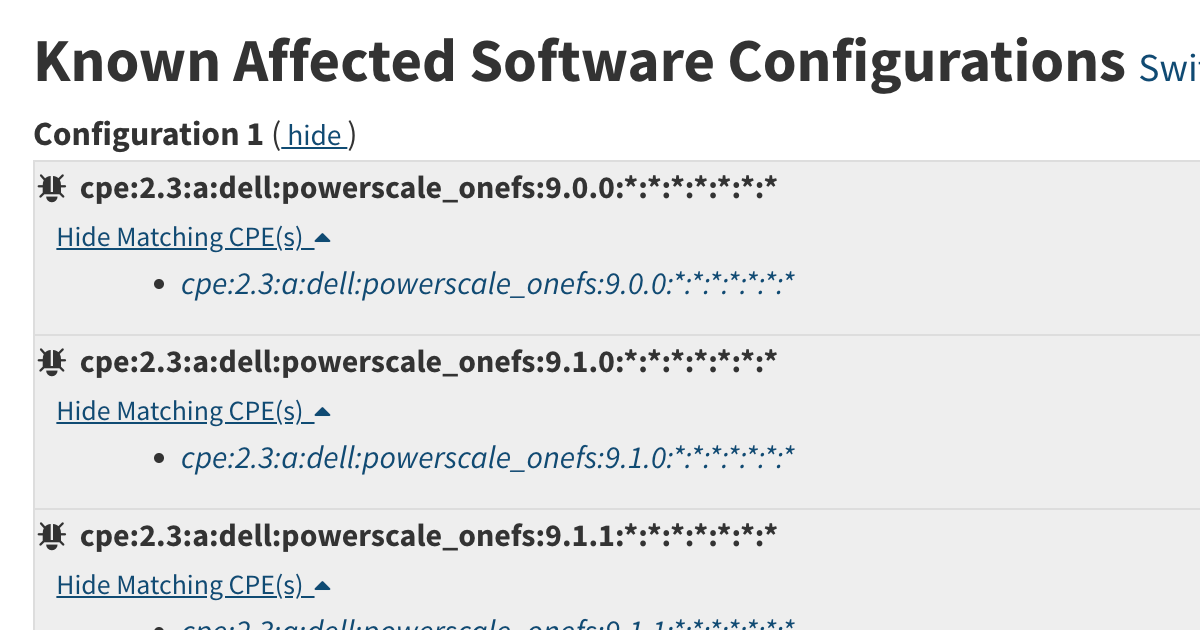
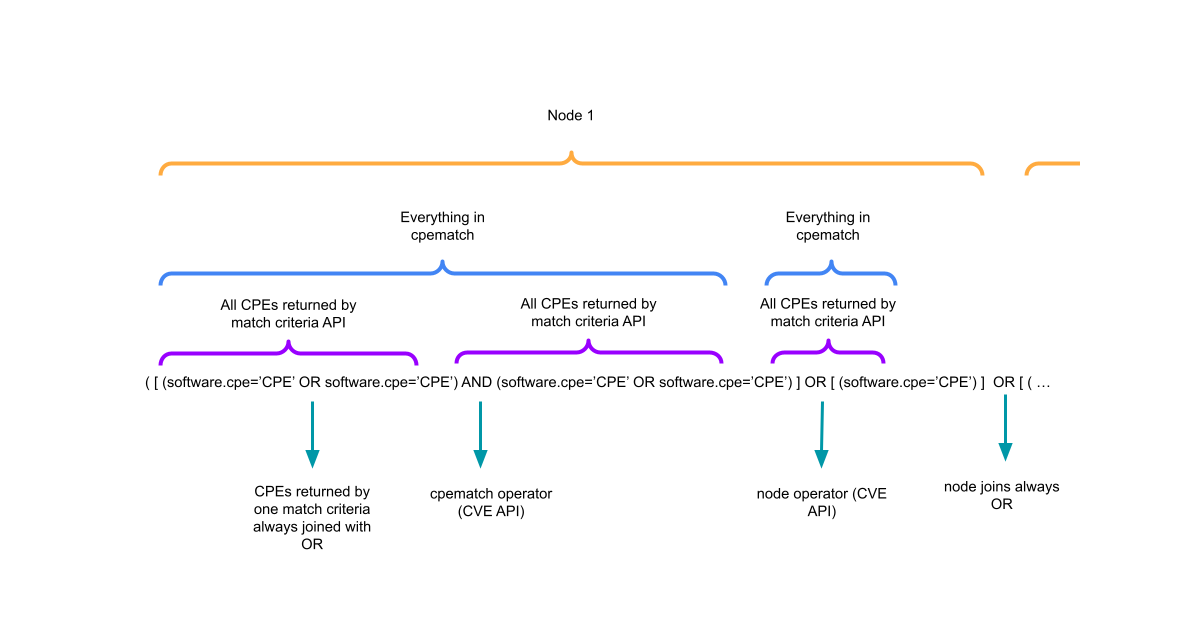
How Known Affected Software Configorations on the CVE Website are Constructed
TUTORIAL August 05, 2024
I wanted to write detection rules to identify what products are vulnerable to a CVE. In this post I walk you through my research. -
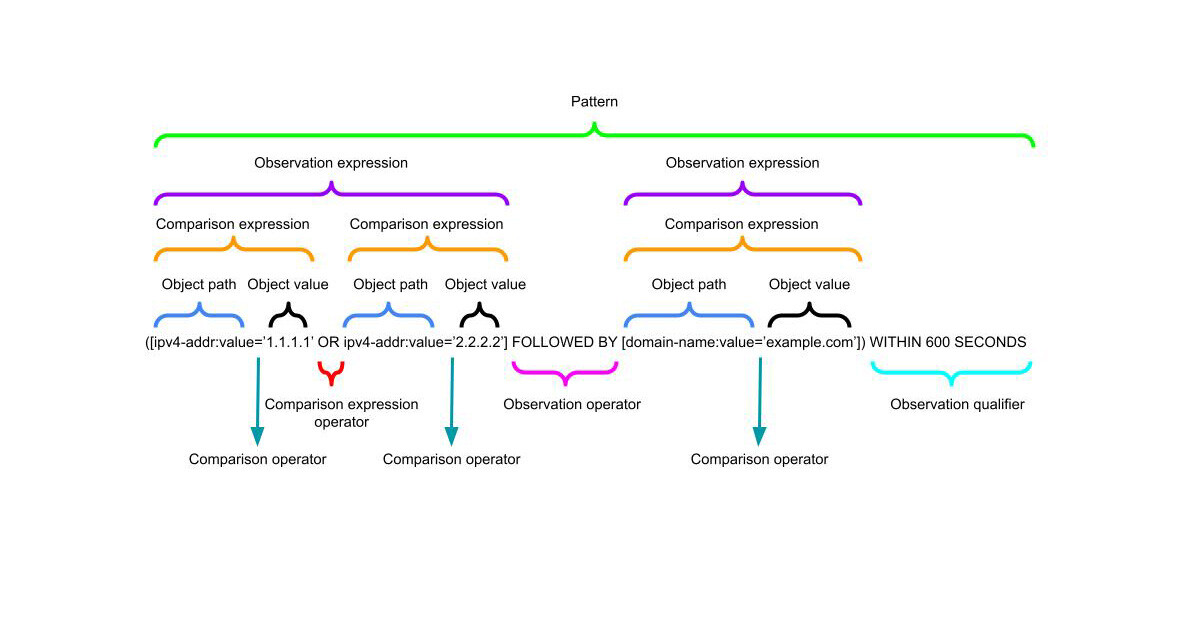
Constructing STIX Indicator Patterns to Write Detection Rules
TUTORIAL July 01, 2024
The STIX 2.1 Indicator SDO specification is flexible enough to allow for a range of detection languages. In this post I will show you how to use the STIX pattern language to write detections using cyber threat intelligence data. -
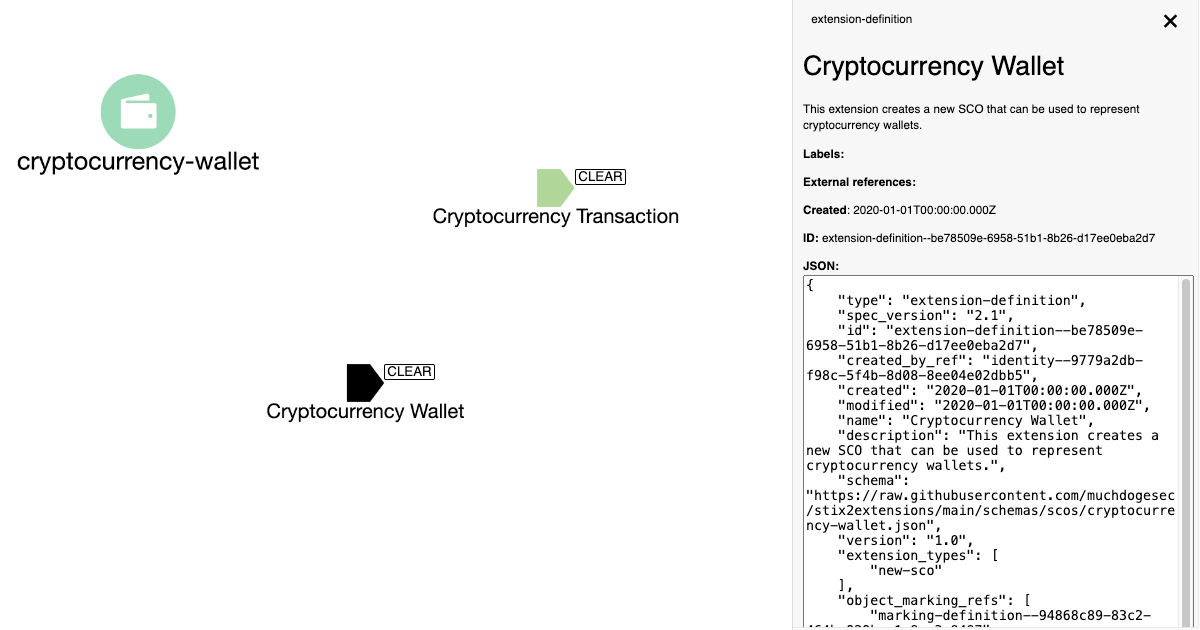
Creating Custom STIX Objects for Cyber Threat Intelligence
TUTORIAL June 24, 2024
Sometimes the default STIX 2.1 objects will not be broad enough for your needs. This post describes how you can extend the STIX specification when required. -
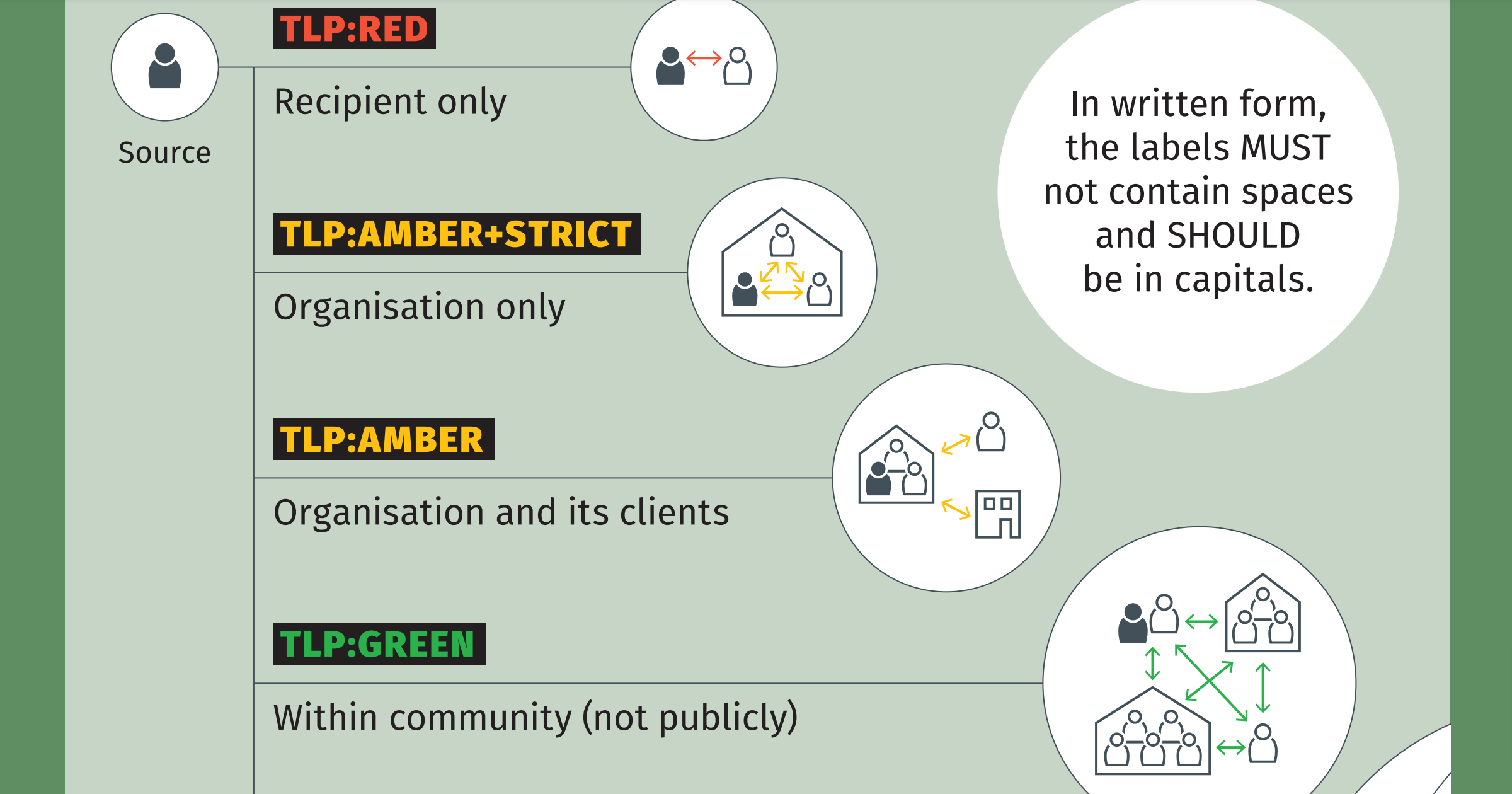
STIX 2.1 support for TLPv2
TUTORIAL June 18, 2024
A short post with code examples that show how to use TLPv2 with STIX 2.1. -
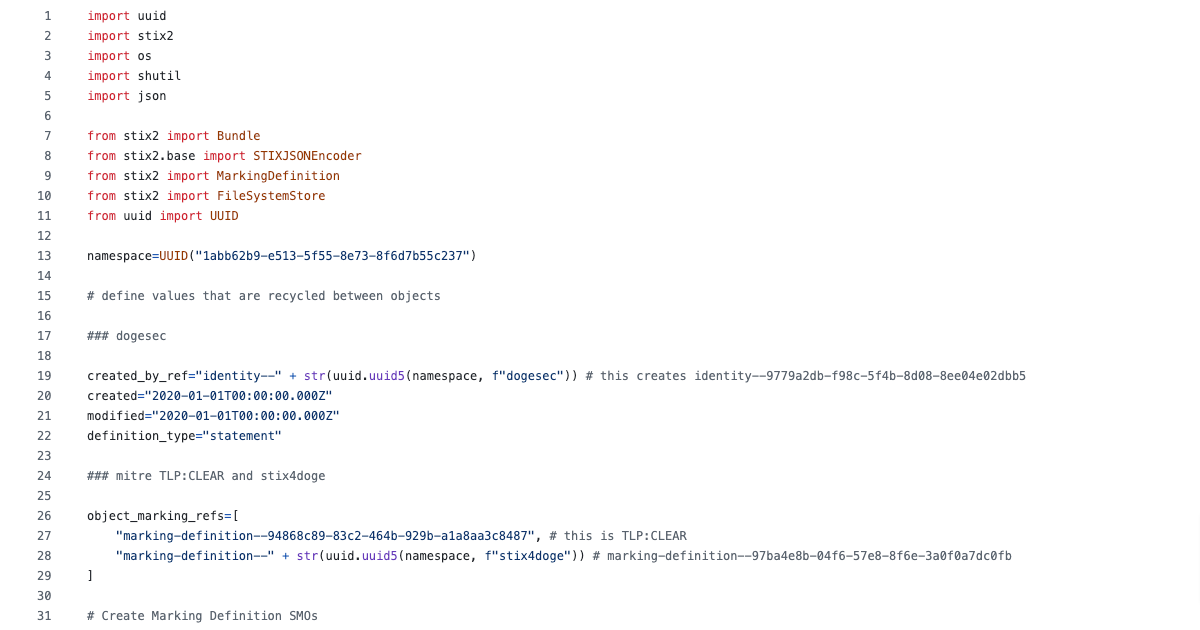
A Quick Start Guide to Generate STIX 2.1 Structured Threat Intelligence using Python
TUTORIAL June 17, 2024
A post full of code examples that will give you everything you need to start creating STIX objects to make it simple to share your threat research. -
A Beginners Guide to Creating Threat Intelligence using STIX 2.1 Objects
TUTORIAL June 10, 2024
STIX 2.1 allows you to tell stories by connecting objects together to form the story-line of cyber actors, campaigns, incidents, and much more. In this post I explain how.