If you are reading this blog post via a 3rd party source it is very likely that many parts of it will not render correctly (usually, the interactive graphs). Please view the post on dogesec.com for the full interactive viewing experience.
tl;dr
For a long time, I, like many of you, have been tagging our detection content with ATT&CK Techniques.
Sometimes, ashamedly, I tout full detection coverage for a particular threat.
I show off the ATT&CK Navigator highlighting how all the detections cover the ATT&CK Techniques an intel team have discovered an adversary to use.
The reality is, although this captures a lot of information, and is often better-than-nothing, it still lacks a key component – time (or flow!)
Many people incorrectly read the ATT&CK Matrix as a flow. They assume the flow of an ATT&CK moves from left to right. This is incorrect in many instances where an attacker jumps backwards and forwards in their attempts to achieve an objective.
The point is this; the ATT&CK Matrix alone does not provide enough to describe how an adversary might work and that’s where Attack Flows come in.
Attack Flows are a language for describing how cyber adversaries combine and sequence various offensive techniques to achieve their goals.
The Attack Flow team maintain some good examples of Attack Flows here. I’d argue this is the best way to quickly figure out what Attack Flows do and how they work.
Below is a screenshot of one of these examples; Black Basta Ransomware Attack Flow
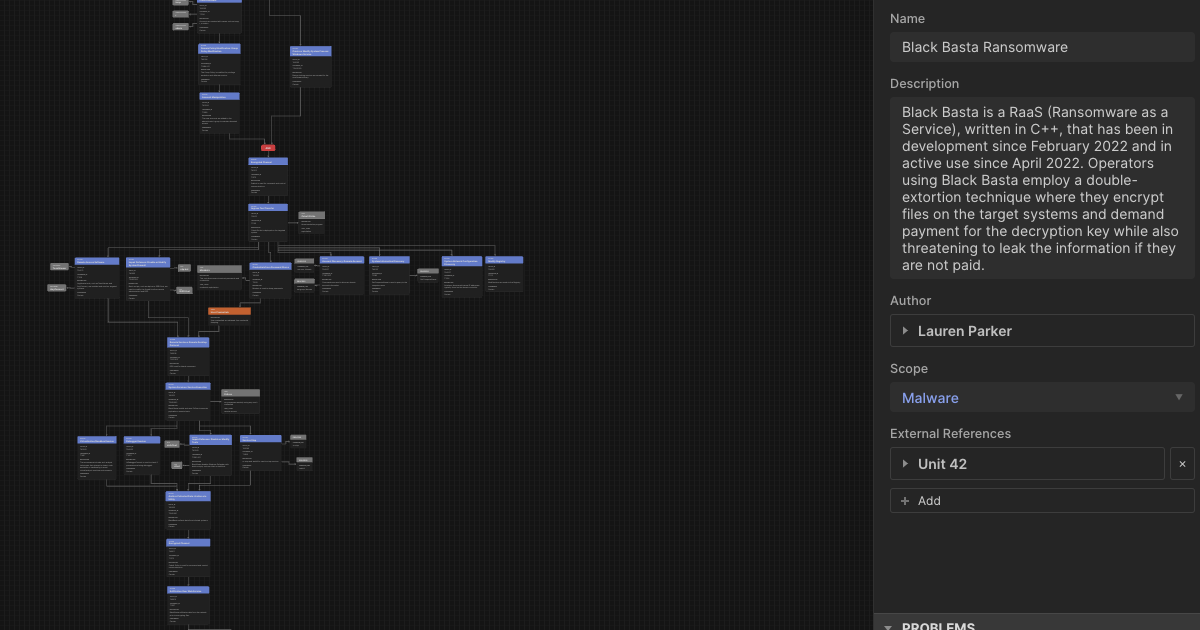
I’ve long been thinking of how we could build Attack Flows into dogesec tooling. For example, instead of just extracting MITRE ATT&CK Techniques from a report using txt2stix, going a step further to understand the order in which these Techniques are logically described in the report.
We’re not there yet, but this post provides a summary of my research from a technical perspective. It’s written for those wanting to understand how Attack Flow works under the hood.
A short note before I begin
Attack Flow is not exclusively tied to MITRE ATT&CK.
In fact, any framework that is represented using Tactics or Techniques, like DISARM or MITRE ATLAS, can be represented using Attack Flows.
For example, you could use MITRE ATLAS objects to model how an attack on a AI systems is performed.
However, for the purpose of this post I am going to focus on ATT&CK for clarity.
Attack Flow + STIX
For long time readers of this blog, and fellow STIX advocates, you’ll be pleased to learn that Attack Flows are built on STIX objects.
If you’re new to STIX Objects or ATT&CK, read the following posts first to bring yourself up-to-speed;
- A Beginners Guide to Creating Threat Intelligence using STIX 2.1 Objects
- Creating Custom STIX Objects for Cyber Threat Intelligence
- PSA: MITRE ATT&CK is More Than Tactics and Techniques
Now let’s jump into the deep-end. Here’s the STIX Bundle for the Black Basta Ransomware Attack Flow referenced earlier.
If you scan through the JSON you will notice core STIX SDO object types in the bundle (e.g. identity and marking-definition).
Of note, you’ll see no MITRE ATT&CK STIX Objects (attack-pattern for Techniques, x-mitre-tactics for Tactics), despite the fact the Attack Flow contains reference to such objects.
Looking at the Attack Flow custom STIX objects explains why this is the case.
At the very top of the example Attack Flow bundle linked for Black Basta you’ll find an extension-definition.
{
"type": "extension-definition",
"id": "extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4",
"spec_version": "2.1",
"created": "2022-08-02T19:34:35.143Z",
"modified": "2022-08-02T19:34:35.143Z",
"name": "Attack Flow",
"description": "Extends STIX 2.1 with features to create Attack Flows.",
"created_by_ref": "identity--fb9c968a-745b-4ade-9b25-c324172197f4",
"schema": "https://center-for-threat-informed-defense.github.io/attack-flow/stix/attack-flow-schema-2.0.0.json",
"version": "2.0.0",
"extension_types": [
"new-sdo"
],
"external_references": [
{
"source_name": "Documentation",
"description": "Documentation for Attack Flow",
"url": "https://center-for-threat-informed-defense.github.io/attack-flow"
},
{
"source_name": "GitHub",
"description": "Source code repository for Attack Flow",
"url": "https://github.com/center-for-threat-informed-defense/attack-flow"
}
]
}
This extension-definition defines the schemas for custom STIX SDO objects employed by Attack Flow.
Which are…
Attack Flow (attack-flow)
Every Attack Flow bundle must contain exactly one Attack Flow object. It provides metadata for name and description, starting points for the flow of actions, and can be referenced from other STIX objects.
This is not directly shown as an object in the Attack Flow, but is shown as metadata for the flow iteself.
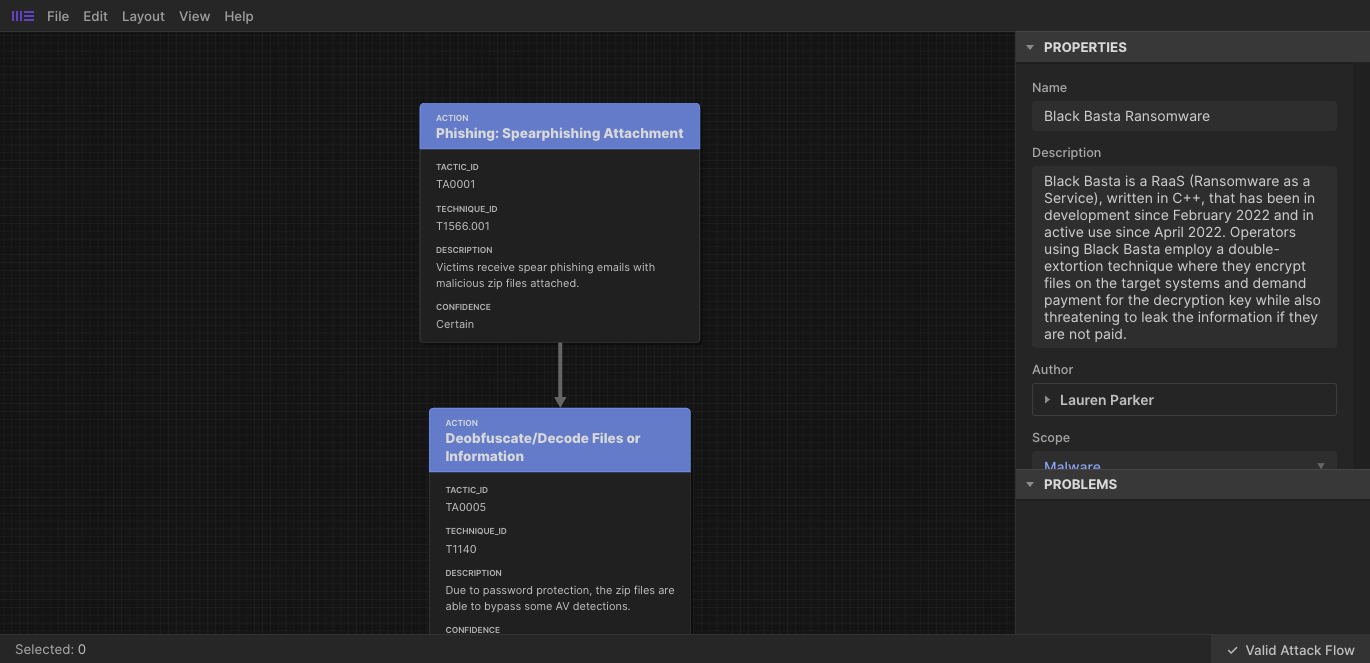
Here is the attack-flow object found in the Black Basta bundle.
{
"type": "attack-flow",
"id": "attack-flow--042142d6-2080-4c1d-8ef2-bad02c39db3b",
"spec_version": "2.1",
"created": "2024-06-19T15:45:49.090Z",
"modified": "2024-11-05T01:11:47.284Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"created_by_ref": "identity--17e98dac-59d5-4d50-b00b-6d95630b205e",
"start_refs": [
"attack-action--a3679838-b02f-4c2b-a0b6-d3450ca2e1dd"
],
"name": "Black Basta Ransomware",
"description": "Black Basta is a RaaS (Ransomware as a Service), written in C++, that has been in development since February 2022 and in active use since April 2022. Operators using Black Basta employ a double-extortion technique where they encrypt files on the target systems and demand payment for the decryption key while also threatening to leak the information if they are not paid.",
"scope": "malware",
"external_references": [
{
"source_name": "Unit 42",
"description": "Threat Assessment ",
"url": "https://unit42.paloaltonetworks.com/threat-assessment-black-basta-ransomware/"
}
]
}
Most of the properties are standard STIX, with the exception of;
scope: Indicates what type of behaviour the Attack Flow describes, eitherincident,campaign,threat-actor,malware,attack-tree,other.start_refs: Contains a list of objects that start the flow. This might be multiple objects as an attack does not usually start with a single technique to try and gain a foothold. Take this flow for a Cobalt Kitty Campaign as an example, the flow starts with a Spearphishing Link AND a Spearphishing Attachment, showing the group was trying both approaches with the aim of performing the Technique T1140, Deobfuscate/Decode Files or Information.
Attack Action (attack-action)
An Attack Action object represents the execution of a particular technique, i.e. a discrete unit of adversary behaviour.
Attack Action tend to be the most common objects in a flow, linked together via references to other Flow objects, typically, but not limited to other Attack Actions.
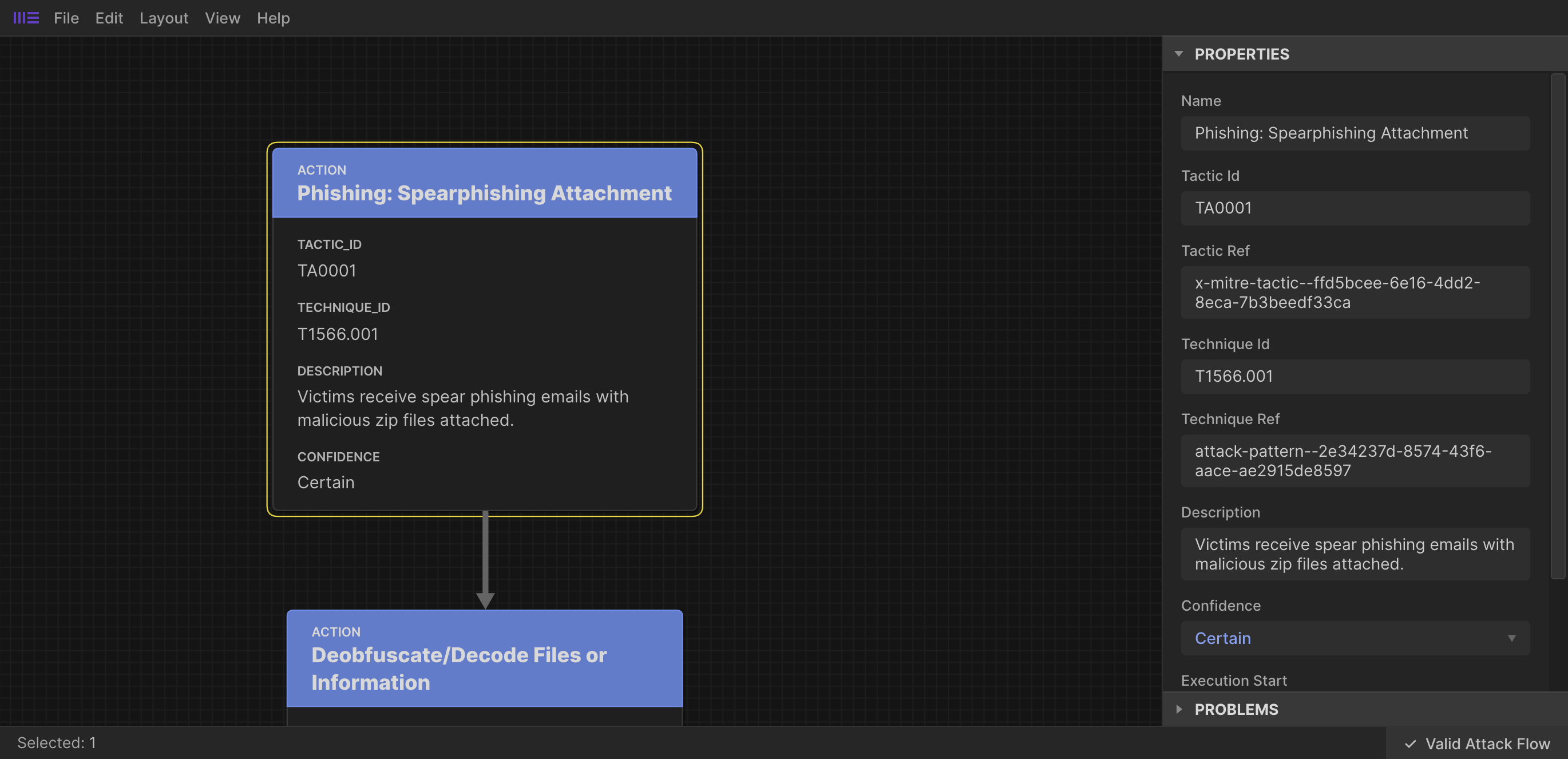
Here’s an example of how those objects are built as STIX;
{
"type": "attack-action",
"id": "attack-action--a3679838-b02f-4c2b-a0b6-d3450ca2e1dd",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.285Z",
"modified": "2024-11-05T01:11:47.285Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "Phishing: Spearphishing Attachment",
"tactic_id": "TA0001",
"tactic_ref": "x-mitre-tactic--ffd5bcee-6e16-4dd2-8eca-7b3beedf33ca",
"technique_id": "T1566.001",
"technique_ref": "attack-pattern--2e34237d-8574-43f6-aace-ae2915de8597",
"description": "Victims receive spear phishing emails with malicious zip files attached.",
"confidence": 100,
"effect_refs": [
"attack-action--b2345e48-33c8-4a67-99cc-7dec00f978cc"
]
},
The key parts in this object include, the reference to the Tactics and/or Techniques;
tactic_id: the ATT&CK ID of the Tactic object, e.g.TA0002tactic_ref: the STIX ID of the Tactictechnique_id: the ID of the Technique object, e.g.T1204.002technique_ref: the STIX ID of the Technique
All of these properties are optional.
You might also be wondering why you need to specify a Technique and a Tactic.
In the MITRE ATT&CK framework, certain techniques belong to multiple tactics because they can be used in different stages of an attack.
Take for example Valid Accounts (T1078), which can be found Initial Access, Persistence, Privilege Escalation, and Defense Evasion. The STIX object ID for Valid Accounts (attack-pattern--b17a1a56-e99c-403c-8948-561df0cffe81) is always the same (and is referenced in all the 4 x-mitre-tactic objects). Thus, referencing the correct Tactic for the Flow is important to define when this Tactic was employed.
Of course, for frameworks where Tactic and Techniques have a 1-1 relationships, the inclusion of a Tactic is not really required (though still very helpful to include for readers).
You can include the ATT&CK STIX objects in the Flow bundle, however, this is optional (because Attack Flow understands ATT&CK natively). However, if you’re using custom frameworks, you should include the tactic and technique objects in the Attack Flow bundle.
Other key properties in Attack Actions are the three that define references, aka the relationships to other Flow objects. These are;
command_ref
Describes tools or commands executed by the attacker by referring to a STIX Process object, which can represent commands, environment variables, process image, etc.
For example the Attack Action could contain the following line;
{
"type": "attack-action",
"id": "attack-action--d4998f70-63bb-439c-a279-282cfddc53fe",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.285Z",
"modified": "2024-11-05T01:11:47.285Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "Service Stop",
"tactic_id": "TA0040",
"tactic_ref": "x-mitre-tactic--5569339b-94c2-49ee-afb3-2222936582c8",
"technique_id": "T1489",
"technique_ref": "attack-pattern--20fb2507-d71c-455d-9b6d-6104461cf26b",
"description": "sc stop and taskkill is used to stop services.",
"confidence": 100,
"command_ref": "process--a72e1773-a037-405e-8b17-a6484b8a9934",
"effect_refs": [
"attack-action--e4784eca-c724-4035-acb4-3fc76cbcb59f"
]
},
Which refers to a process object (included in the ATT&CK flow bundle) describing a command line command;
{
"type": "process",
"id": "process--a6a24d6c-9089-466b-9da2-b6ca5dd65d23",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.286Z",
"modified": "2024-11-05T01:11:47.286Z",
"command_line": "taskkill"
},
Visually this looks as follows;
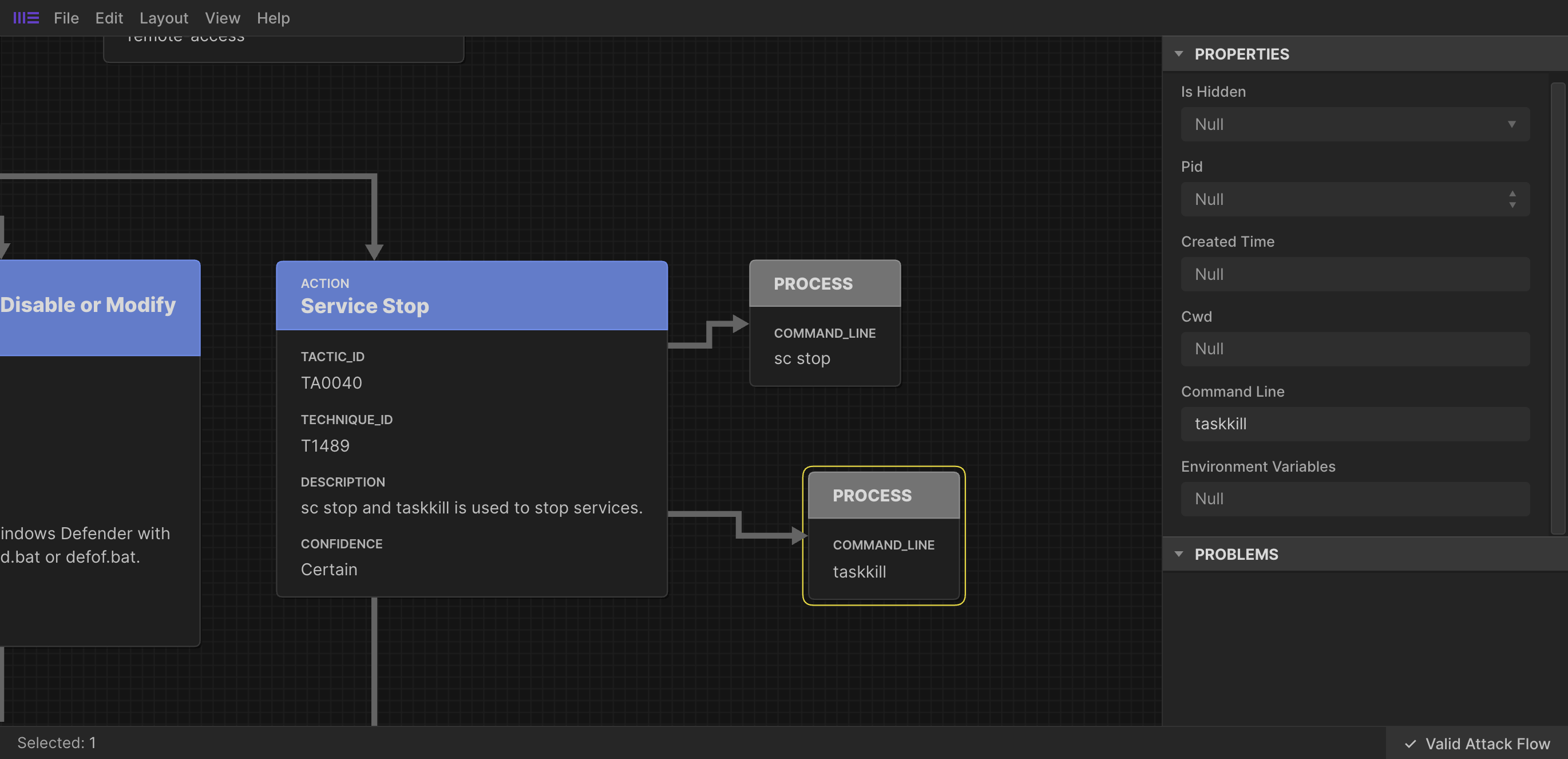
asset_refs
Details the assets involved in this action, i.e. where this action modifies or depends on the state of the asset. These should always be Attack Asset objects, which I’ll cover later in this post.
For example the Attack Action object might contain;
{
"type": "attack-action",
"id": "attack-action--2d4931da-3298-420c-ace1-582fabc4a558",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.285Z",
"modified": "2024-11-05T01:11:47.285Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "Credentials from Password Stores",
"tactic_id": "TA0006",
"tactic_ref": "x-mitre-tactic--2558fd61-8c75-4730-94c4-11926db2a263",
"technique_id": "T1555",
"technique_ref": "attack-pattern--3fc9b85a-2862-4363-a64d-d692e3ffbee0",
"description": "Mimkatz is used to dump passwords.",
"confidence": 100,
"asset_refs": [
"attack-asset--31b2f0db-4950-438a-af27-17d5c8602d3c"
]
},
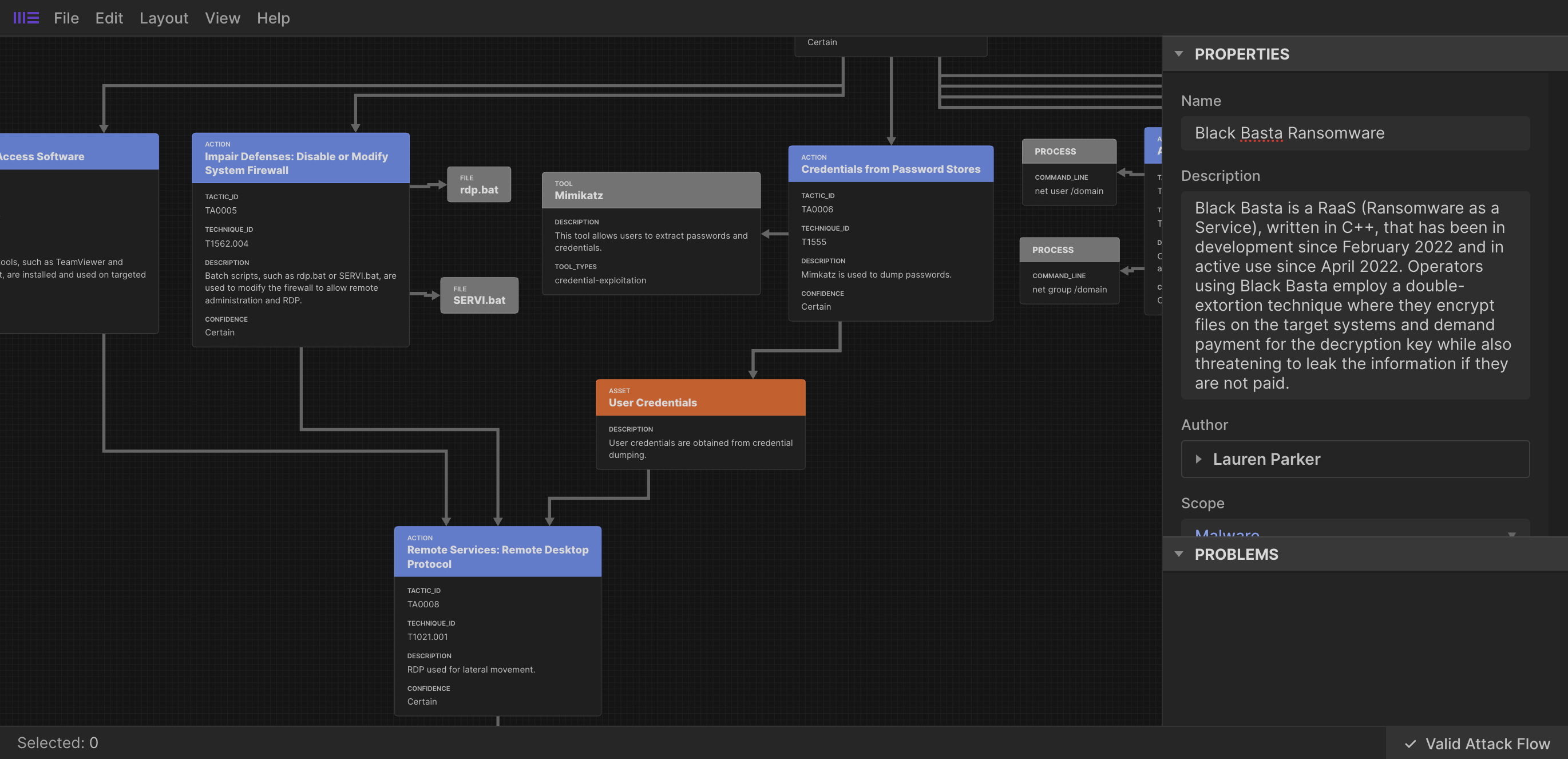
Which refers to the following Asset (user credentials);
{
"type": "attack-asset",
"id": "attack-asset--31b2f0db-4950-438a-af27-17d5c8602d3c",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.286Z",
"modified": "2024-11-05T01:11:47.286Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "User Credentials",
"description": "User credentials are obtained from credential dumping.",
"object_ref": "attack-action--bfc59d4e-32d1-42ae-94f7-8a1bc4d6dc91"
},
Visually this looks as follows;
effect_refs
Lists the potential effects that result from executing this action. This could refer to other Attack Action objects, or Attack Operator or Attack Condition objects both of which I’ll cover in more detail later in the post.
For example;
{
"type": "attack-action",
"id": "attack-action--c14c8d17-1a12-439b-aef4-a2f1e66052ea",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.285Z",
"modified": "2024-11-05T01:11:47.285Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "System Services: Service Execution",
"tactic_id": "TA0002",
"tactic_ref": "x-mitre-tactic--4ca45d45-df4d-4613-8980-bac22d278fa5",
"technique_id": "T1569.002",
"technique_ref": "attack-pattern--f1951e8a-500e-4a26-8803-76d95c4554b4",
"description": "Black Basta installs and uses PsExec to execute payloads on remote hosts.",
"confidence": 100,
"effect_refs": [
"attack-action--d4998f70-63bb-439c-a279-282cfddc53fe",
"attack-action--3a7cc2d4-25fe-4fb5-abee-5f2b6dc0caee",
"attack-action--a22fdaff-b20e-4896-ac6c-81a93ddb36df",
"attack-action--93a4a781-5805-494a-9d93-6cf72577876a"
]
},
You can see visually this links to four other Actions;
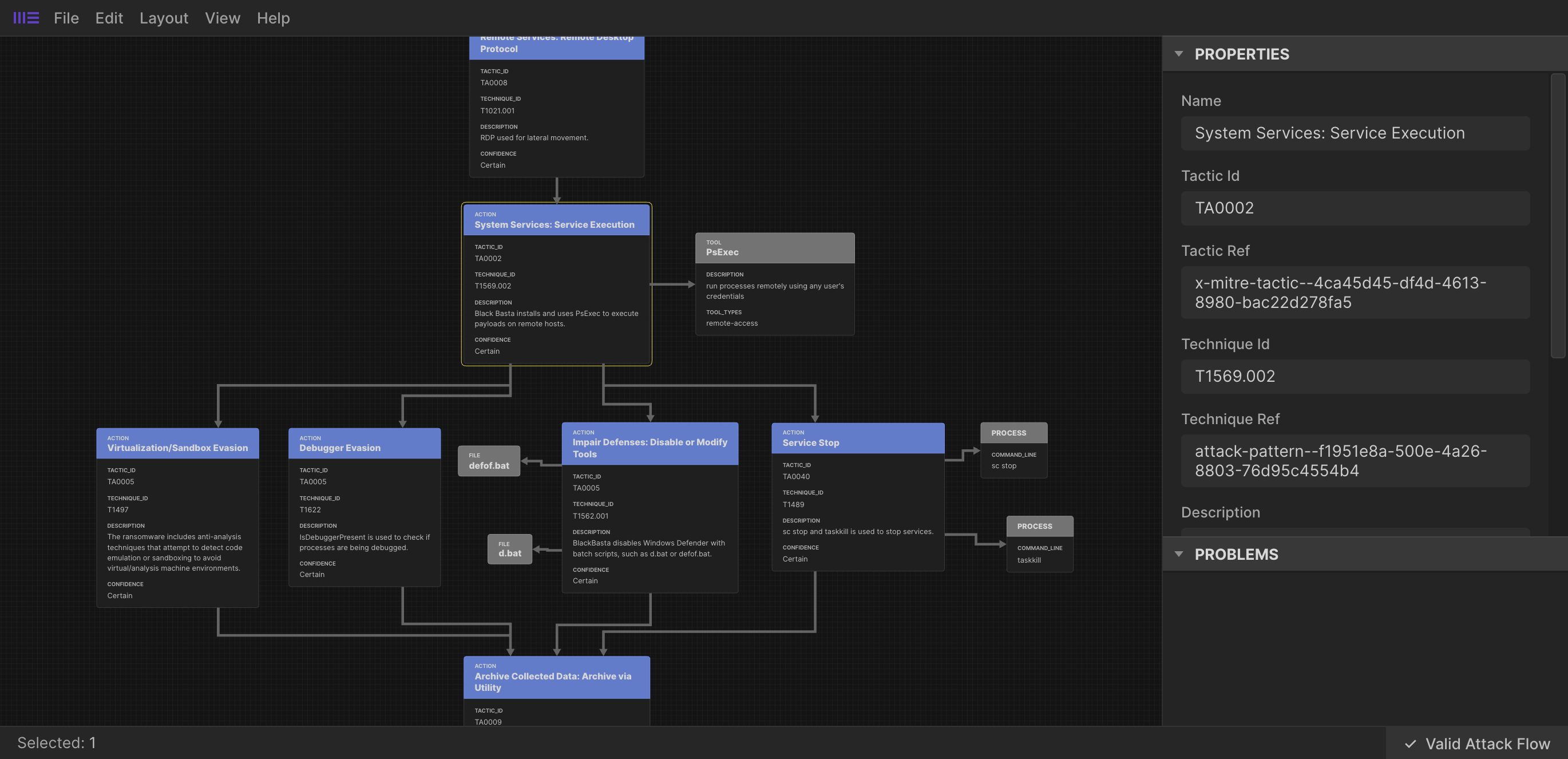
effect_refs are the most commonly used references in Attack Flow objects to define the next logical step in the flow.
Attack Asset (attack-asset)
An Attack Asset object is any object that is the subject or target of an action. Assets can be technical assets (such as machines and data) or non-technical assets such as people and physical systems. Actions typically either modify or depend upon the state of an asset in some way.
For example non-specific user credentials,
{
"type": "attack-asset",
"id": "attack-asset--31b2f0db-4950-438a-af27-17d5c8602d3c",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.286Z",
"modified": "2024-11-05T01:11:47.286Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "User Credentials",
"description": "User credentials are obtained from credential dumping.",
"object_ref": "attack-action--bfc59d4e-32d1-42ae-94f7-8a1bc4d6dc91"
},
Port scanning
{
"type": "attack-asset",
"id": "attack-asset--435e40bd-19a7-4099-8a32-0c268760b218",
"spec_version": "2.1",
"created": "2024-11-05T01:11:50.613Z",
"modified": "2024-11-05T01:11:50.613Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "Port Scanning",
"description": "scanned SMB, TCP 5000, TCP 9392, and TCP 6106. Actors were looking for backup products Synology, Backup Exec, and Veeam"
},
An Attack Asset object can also contain a reference (object_ref) to any STIX data object (i.e. SDO) or observable (i.e. SCO) that contains structured data about this asset. For example;
{
"type": "attack-asset",
"id": "attack-asset--5680cc87-1401-43a5-aced-07ad9848b900",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.400Z",
"modified": "2024-11-05T01:11:47.400Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"name": "VMWare Server",
"description": "vulnerable, public-facing server",
"object_ref": "software--d49a2f00-aad8-5002-8583-bcd456125da1"
}
{
"type": "software",
"spec_version": "2.1",
"id": "software--d49a2f00-aad8-5002-8583-bcd456125da1",
"name": "cpe:2.3:a:vmware:vmware_server:1.0.5:*:*:*:*:*:*:*",
"cpe": "cpe:2.3:a:vmware:vmware_server:1.0.5:*:*:*:*:*:*:*",
"vendor": "vmware",
"version": "1.0.5",
"object_marking_refs": [
"marking-definition--94868c89-83c2-464b-929b-a1a8aa3c8487",
"marking-definition--562918ee-d5da-5579-b6a1-fae50cc6bad3"
],
"extensions": {
"extension-definition--82cad0bb-0906-5885-95cc-cafe5ee0a500": {
"extension_type": "toplevel-property-extension"
}
},
"x_cpe_struct": {
"cpe_version": "2.3",
"edition": "*",
"language": "*",
"other": "*",
"part": "a",
"vendor": "vmware",
"product": "vmware_server",
"version": "1.0.5",
"sw_edition": "*",
"target_hw": "*",
"target_sw": "*",
"update": "*"
}
},
You should package these STIX objects in the Attack Flow bundle too.
Attack Condition (attack-condition)
An Attack Condition object represents some possible condition, outcome, or state that could occur. Conditions can be used to split flows based on the success or failure of an action, or to provide further description of an actions results.
{
"type": "attack-condition",
"id": "attack-condition--e9da9ad8-37a3-4bbe-9ec7-95cfab867d96",
"spec_version": "2.1",
"created": "2024-11-05T01:11:48.136Z",
"modified": "2024-11-05T01:11:48.136Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"description": "IcedID malware went quiet for 2 days",
"on_true_refs": [
"attack-action--fd17c242-ee9e-46e7-ae64-034a61b80260"
]
},
These objects contain an optional logical condition, either on_true_refs (shown above) or on_false_refs. These properties can contain lists of Attack Actions, Operators or other Conditions.
For example, the Attack Condition above logically reads; if IcedID malware went quiet for 2 days go to Attack Action attack-action--fd17c242-ee9e-46e7-ae64-034a61b80260.
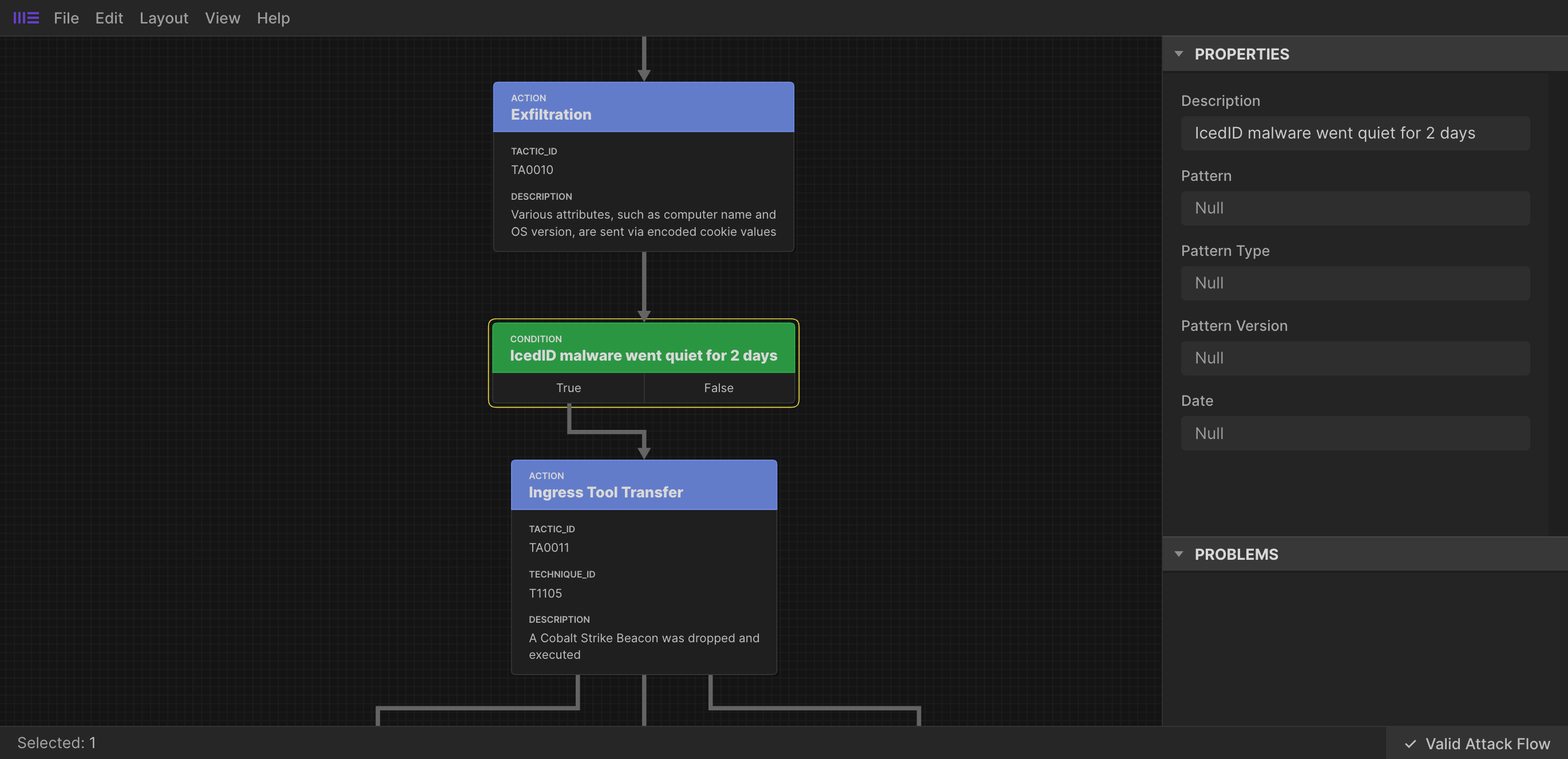
Attack Condition are also very useful to include detection rules in Attack Flows. Whilst an experimental feature at the time of writing, you can also use patterns (aka detection rules) to define the condition.
Here’s another example of an Attack Condition object, this time referencing a Sigma Rule;
{
"type": "attack-condition",
"id": "attack-condition--04909a01-a566-472f-9d71-04bd7195385f",
"spec_version": "2.1",
"created": "2022-11-08T00:00:00.000Z",
"modified": "2023-01-22T00:00:00.000Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
},
"pattern": "{'title': 'Microsoft IIS Service Account Password Dumped', 'id': '2d3cdeec-c0db-45b4-aa86-082f7eb75701', 'status': 'experimental', 'description': 'Detects the Internet Information Services (IIS) command-line tool, AppCmd, being used to list passwords', 'references': ['https://www.elastic.co/guide/en/security/current/microsoft-iis-service-account-password-dumped.html', 'https://twitter.com/0gtweet/status/1588815661085917186?cxt=HHwWhIDUyaDbzYwsAAAA', 'https://www.netspi.com/blog/technical/network-penetration-testing/decrypting-iis-passwords-to-break-out-of-the-dmz-part-2/'], 'author': 'Tim Rauch, Janantha Marasinghe', 'date': '2022/11/08', 'modified': '2023/01/22', 'tags': ['attack.credential_access', 'attack.t1003'], 'logsource': {'category': 'process_creation', 'product': 'windows'}, 'detection': {'selection_base_name': [{'Image|endswith': '\\\\appcmd.exe'}, {'OriginalFileName': 'appcmd.exe'}], 'selection_base_list': {'CommandLine|contains': 'list '}, 'selection_standalone': {'CommandLine|contains': [' /config', ' /xml', ' -config', ' -xml']}, 'selection_cmd_flags': {'CommandLine|contains': [' /@t', ' /text', ' /show', ' -@t', ' -text', ' -show']}, 'selection_cmd_grep': {'CommandLine|contains': [':\\\\*', 'password']}, 'condition': 'all of selection_base_* and (selection_standalone or all of selection_cmd_*)'}, 'falsepositives': ['Unknown'], 'level': 'high'}",
"pattern_type": "sigma",
"description": "Microsoft IIS Service Account Password Dumped",
"on_true_refs": [
"attack-action--70a41be5-2f3d-4c5b-b7d8-938205faf33b"
]
},
When the defined Sigma rule is triggered (on_true_refs) the flow moves to the Attack Action attack-action--70a41be5-2f3d-4c5b-b7d8-938205faf33b.
Attack Operator (attack-operator)
An Attack Operator object joins multiple attack paths together using boolean logic.
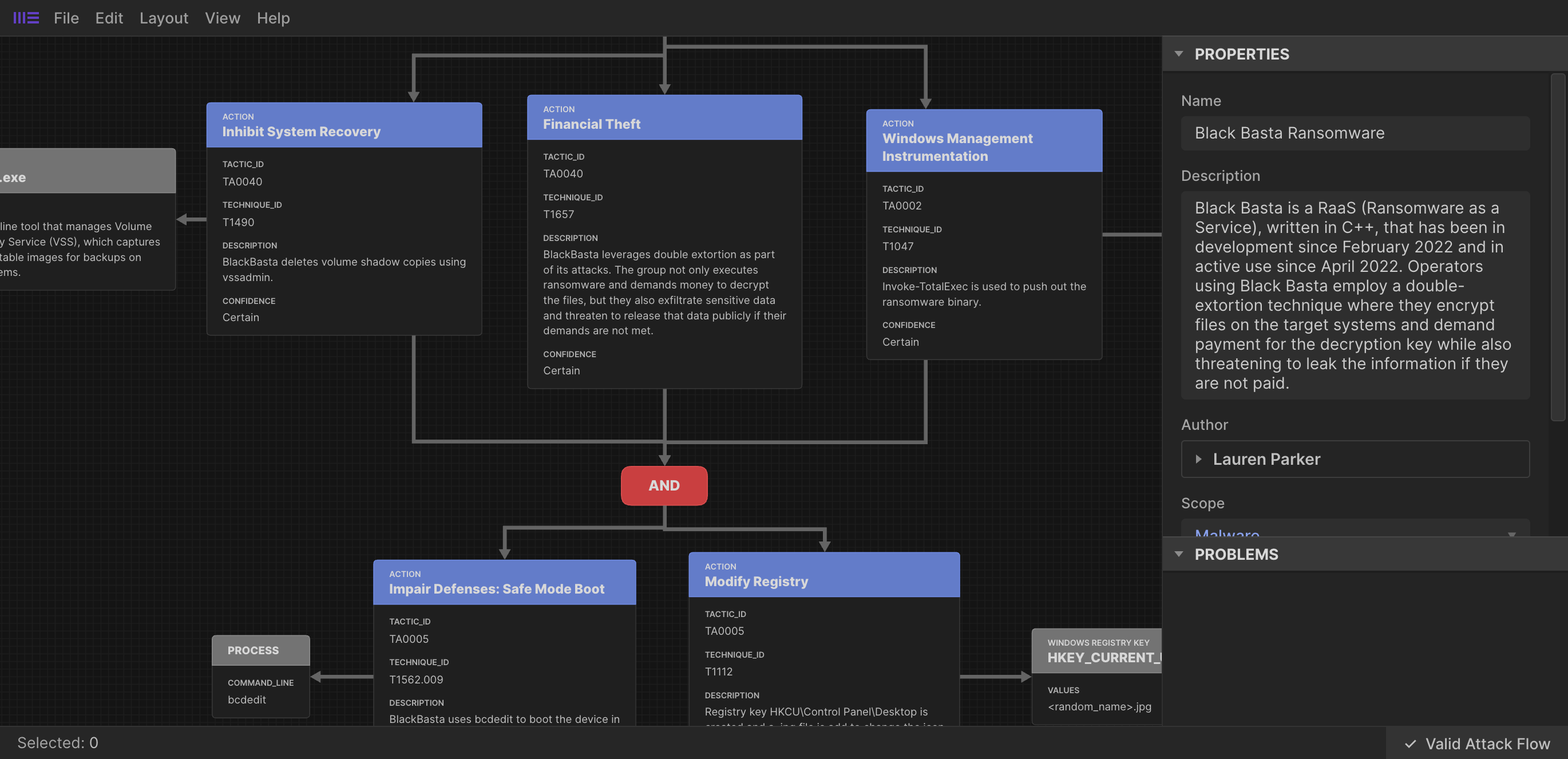
Here is the AND operator object shown in the screenshot;
{
"type": "attack-operator",
"id": "attack-operator--9183210d-5db6-4fd9-bc57-5848734736d3",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.285Z",
"modified": "2024-11-05T01:11:47.285Z",
"extensions": {
"extension-definition--fb9c968a-745b-4ade-9b25-c324172197f4": {
"extension_type": "new-sdo"
}
},
"operator": "AND",
"effect_refs": [
"attack-action--d09fa5d5-e991-4085-a8be-46d62ee28a7f",
"attack-action--ab3bbdcf-9899-4fa9-9365-52d416300957"
]
},
Essentially it is saying; when either of the three flows that refer to this Attack Operator are seen, then both of the Attack Actions listed as effect_refs are seen next.
The OR operator can also be used. If used in the above example, it would logically read; when either of the three flows that refer to this Attack Operator are seen, then either of the two Attack Actions listed as effect_refs are seen next.
Core STIX Object
The eagle eyed readers might have noticed direct references to core STIX object in the Attack Flow bundle.
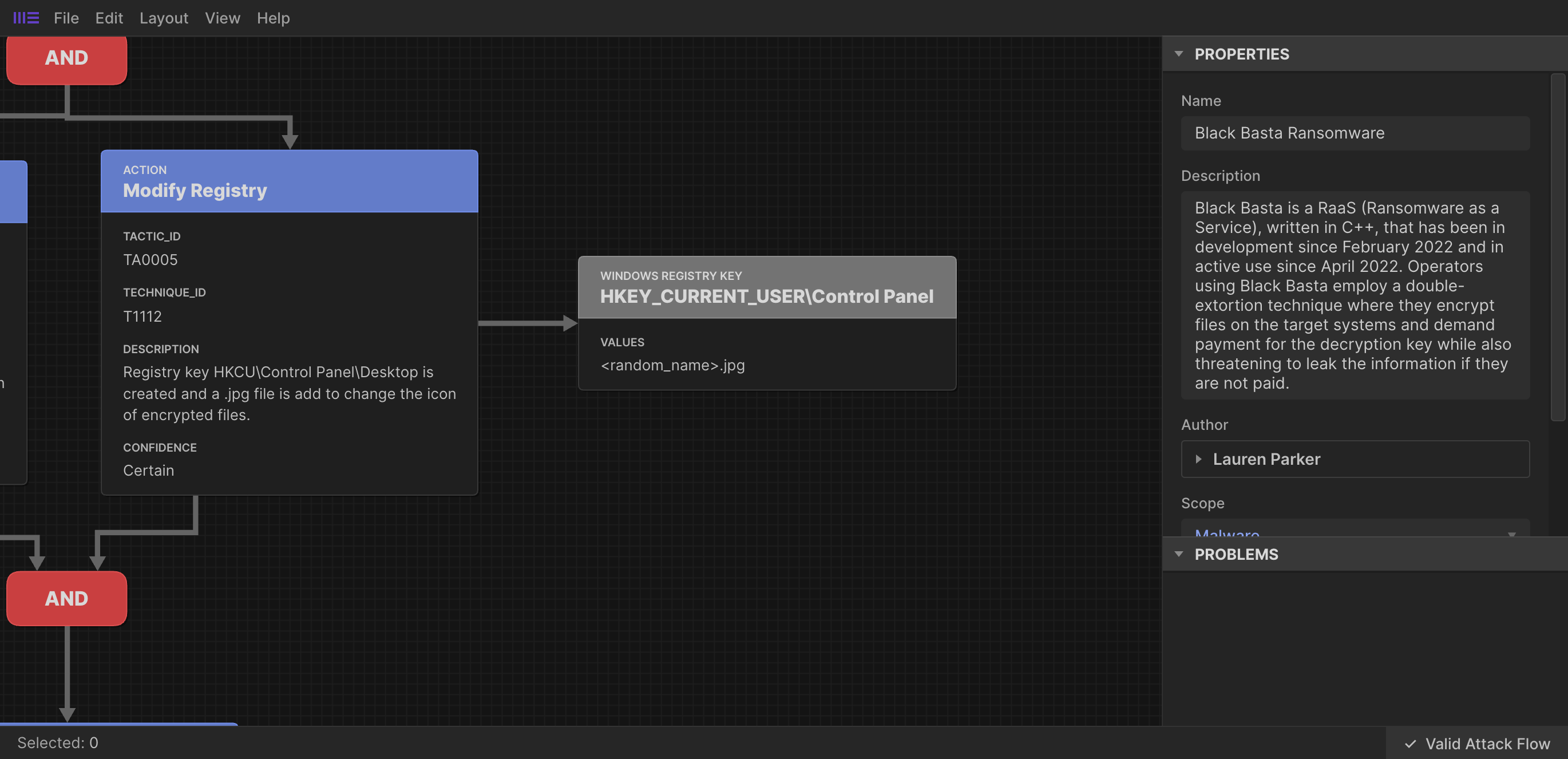
You can use STIX relationship objects to include direct reference between Attack Flow objects and other STIX objects where an appropriate Attack Flow property (e.g. effect_refs) does not suit your requirements.
Here’s how the Windows Registry Key shown above is joined to the Attack Flow Action object;
{
"type": "windows-registry-key",
"id": "windows-registry-key--98145823-cd60-4ea0-8733-93ec0ffc6947",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.286Z",
"modified": "2024-11-05T01:11:47.286Z",
"key": "HKEY_CURRENT_USER\\Control Panel",
"values": [
{
"name": "Wallpaper",
"data": "<random_name>.jpg",
"data_type": "REG_SZ"
}
]
},
{
"type": "relationship",
"id": "relationship--47c08f5d-f31b-4966-9a7f-4d69c8863697",
"spec_version": "2.1",
"created": "2024-11-05T01:11:47.286Z",
"modified": "2024-11-05T01:11:47.286Z",
"relationship_type": "related-to",
"source_ref": "attack-action--d09fa5d5-e991-4085-a8be-46d62ee28a7f",
"target_ref": "windows-registry-key--98145823-cd60-4ea0-8733-93ec0ffc6947"
},
Attack Flow automation
txt2stix has supported the ability to extract ATT&CK related data from text reports for a long time.
We’ve recently added the ability to extract Attack Flows too!
Creating the text file attack_flow_demo.txt;
Victims receive spear phishing emails with from [email protected] malicious zip files attached named badfile.zip
Due to password protection, the zip files are able to bypass some AV detections.
The zip files are extracted and usually contain a malicious document, such as a .doc, .pdf, or .xls. Some examples are malware.pdf and bad.com
The extracted files contain malicious macros that connect to a C2 server 1.1.1.1
Running it through txt2stix;
python3 txt2stix.py \
--relationship_mode ai \
--ai_settings_relationships openai:gpt-4o \
--input_file tests/data/manually_generated_reports/attack_flow_demo.txt \
--name 'Test MITRE ATT&CK Flow demo with iocs' \
--tlp_level clear \
--confidence 100 \
--use_extractions ai_mitre_attack_enterprise,'pattern_*' \
--ai_settings_extractions openai:gpt-4o \
--ai_create_attack_flow \
--report_id 3b160a8d-12dd-4e7c-aee8-5af6e371b425
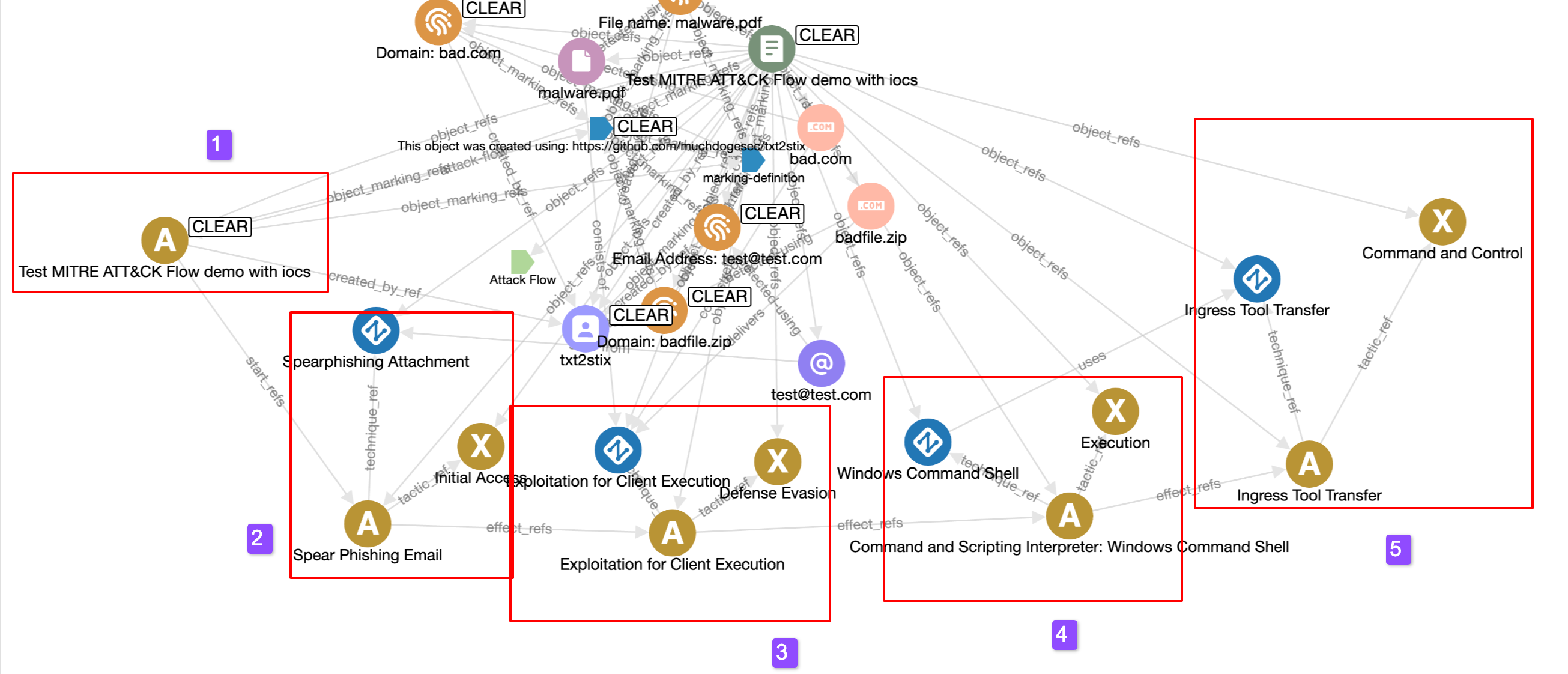
Produces the following bundle;
Below I have tried to illustrate the order of Attack Flow objects (and ATT&CK Tactics and Techniques captured in the Attack Flow Action objects).
SIEM Rules
Your detection engineering AI assistant. Turn cyber threat intelligence research into highly-tuned detection rules.

CTI Butler
One API. Much CTI. CTI Butler is the API used by the world's leading cyber-security companies.
Discuss this post
Head on over to the dogesec community to discuss this post.

Never miss an update
Sign up to receive new articles in your inbox as they published.
