Blog
The dogesec blog
-
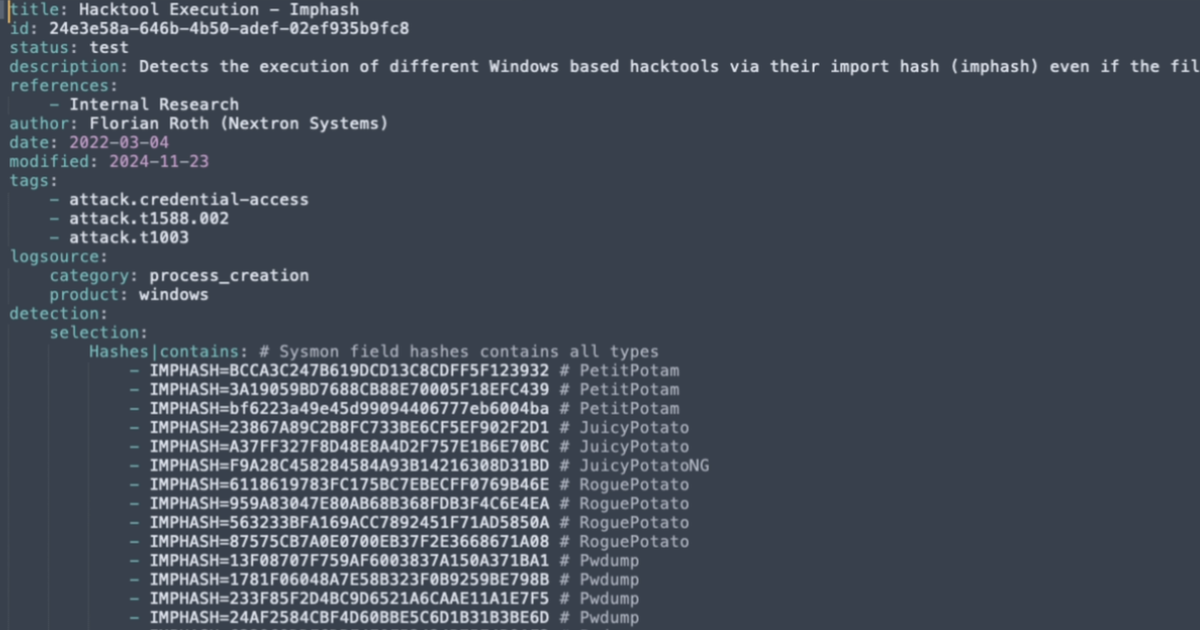
Writing Effective Sigma Detection Rules: A Guide for Novice Detection Engineers
TUTORIAL September 23, 2024
Sigma Rules are becoming more widely adopted as the standard detection language. Learning how to write them is not difficult. Let me show you. -
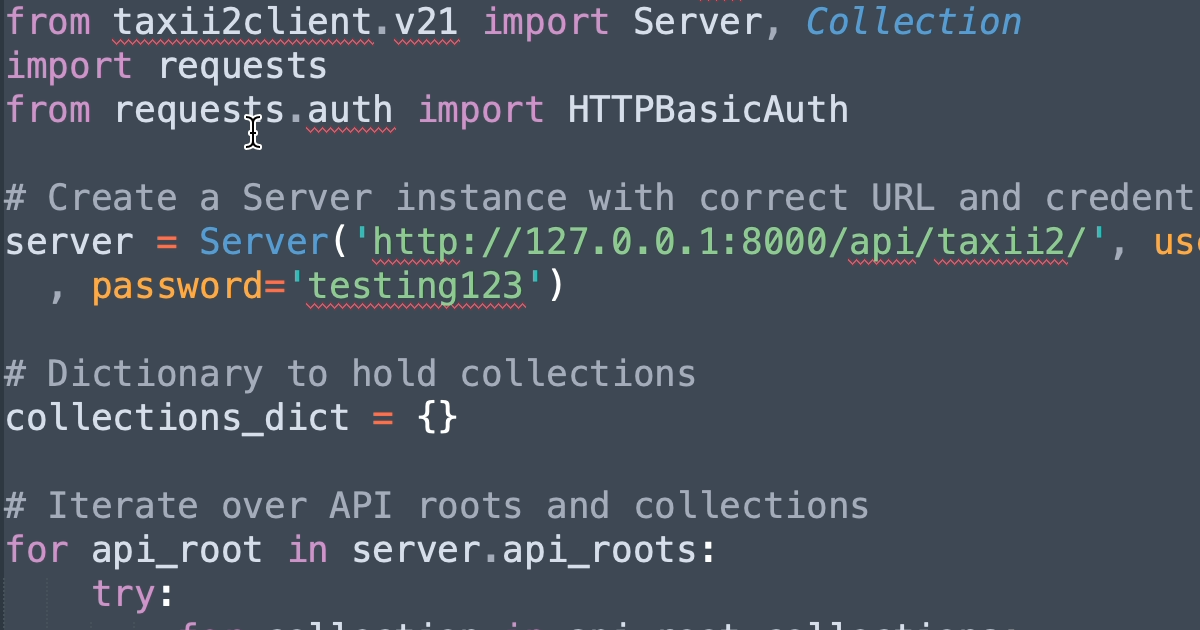
A Deeper Look at a TAXII Client
PRODUCTS September 16, 2024
We built an open-source TAXII server, Arango TAXII Server. Here are some examples of how you can consume data from it using a TAXII Client. -
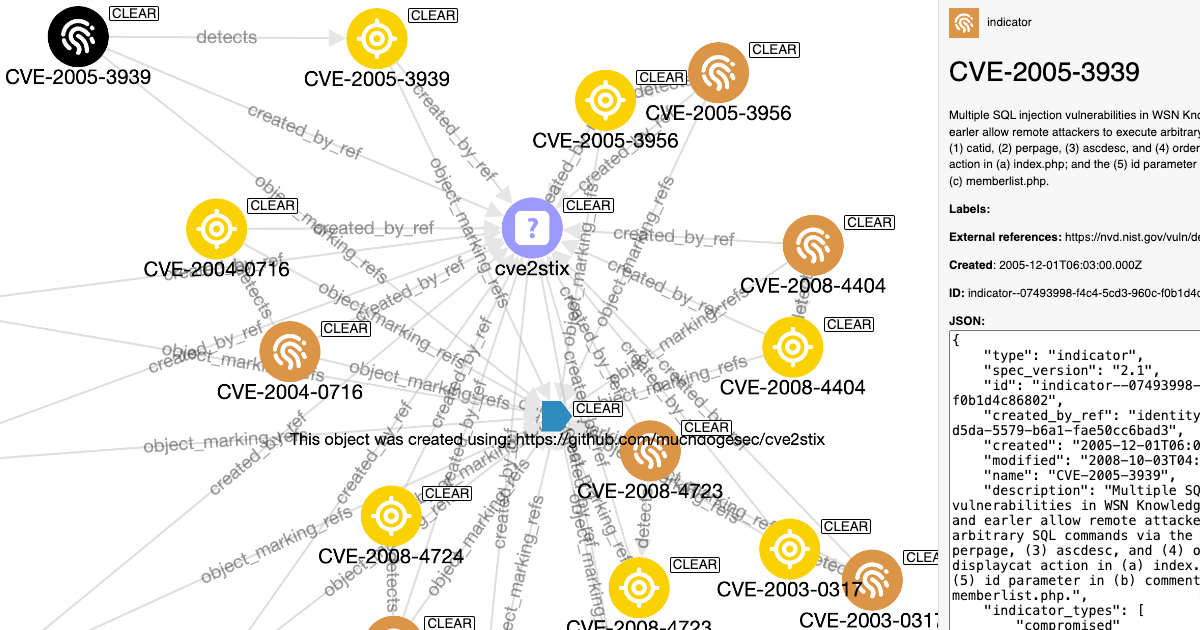
Using STIX Objects to Make Vulnerability Prioritisation Easy (and Free)
TUTORIAL September 02, 2024
Follow along as I show you how to store 200,000 CVEs as STIX objects, then use CVSS, EPSS, CISA KEV and CPE data to search and filter them. -
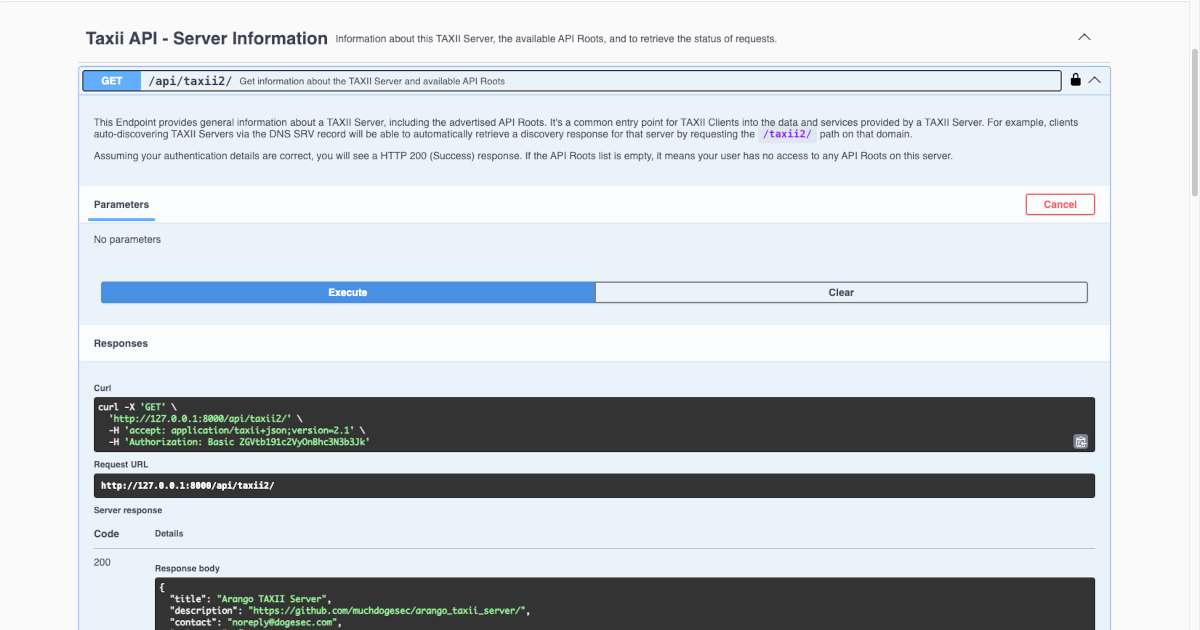
A Producers Guide to Sharing Cyber Threat Intelligence
PRODUCTS August 26, 2024
txt2stix + stix2arango + arango_taxii_server = a robust and flexible setup for storing and distributing cyber threat intelligence you've produced. -
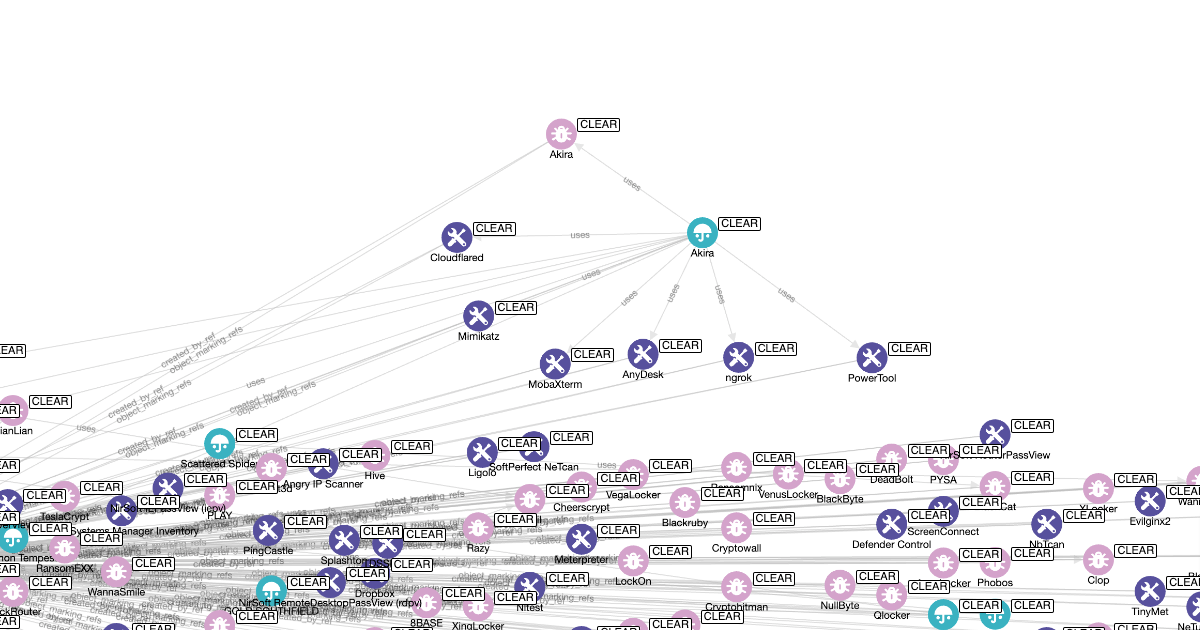
A MITRE ATT&CK Style Knowledge Base for Ransomware
PRODUCTS August 19, 2024
After becoming ever-more frustrated by intelligence producers naming the same ransomware slightly differently, and with ATT&CK missing lots of ransomware types, I finally got around to trying to solve the problem. -
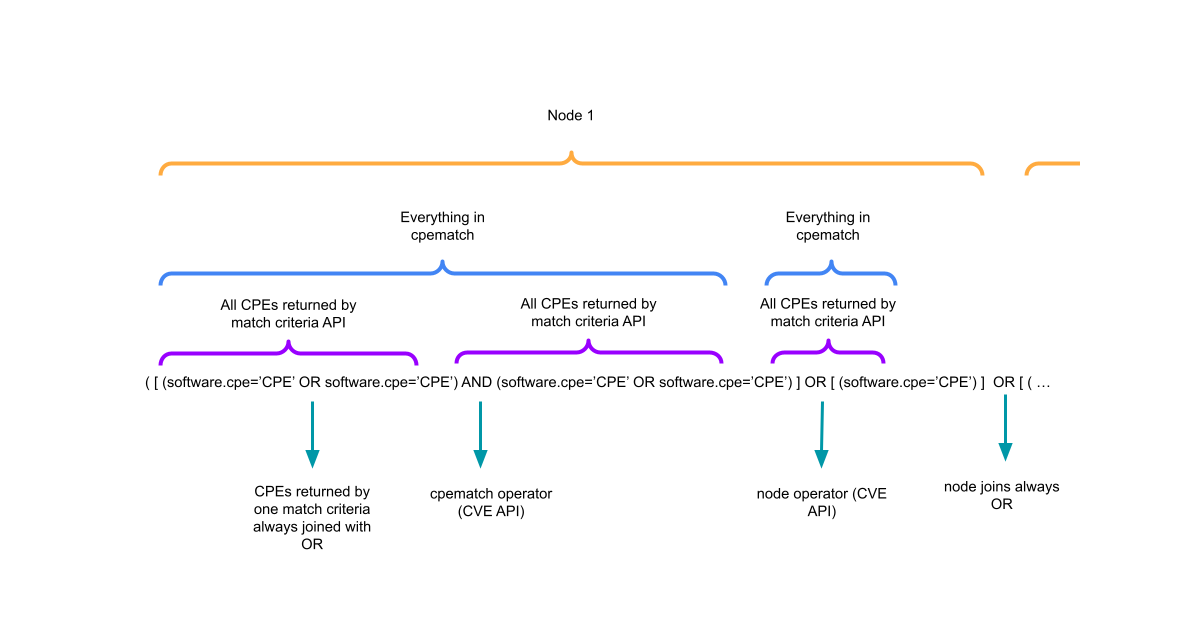
Writing Detection Rules to Identify if Products in my Stack are Vulnerable
TUTORIAL August 12, 2024
Developing on last weeks post, I show you how to construct STIX Patterns to automatically flag which products are affected by published CVEs. -
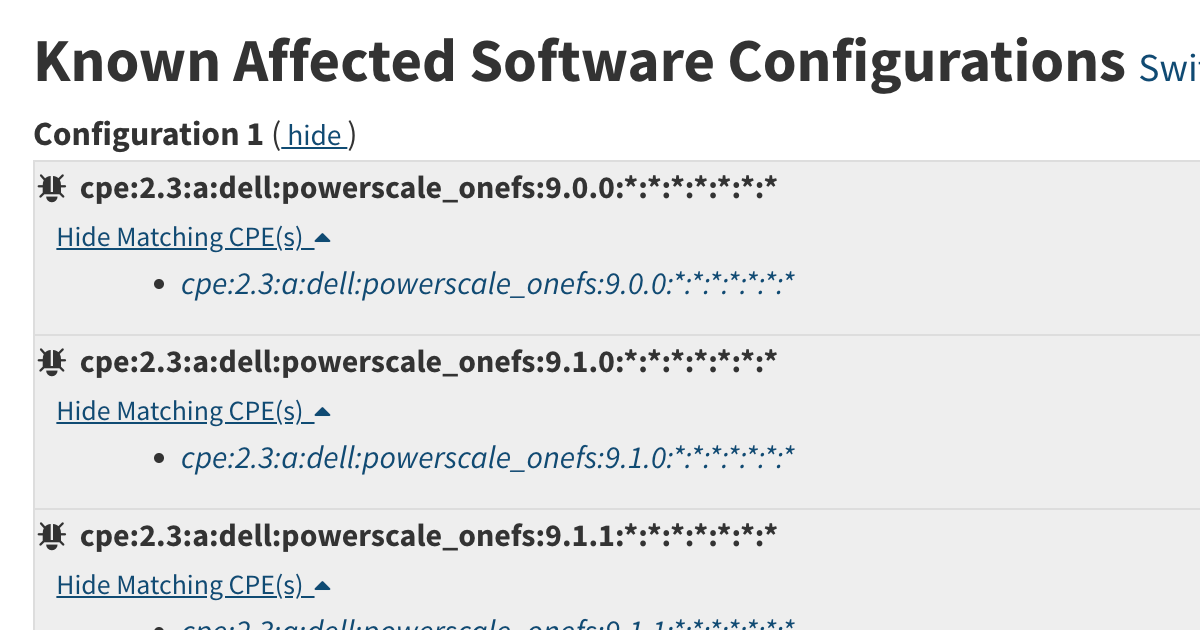
How Known Affected Software Configorations on the CVE Website are Constructed
TUTORIAL August 05, 2024
I wanted to write detection rules to identify what products are vulnerable to a CVE. In this post I walk you through my research. -

Graphing Credit Card Data Leaks Using STIX 2.1 Objects
PRODUCTS July 29, 2024
Turn card numbers into STIX 2.1 objects. Enrich the data with issuer information. Track transactions made by the card. Then link the cards and transactions to other STIX objects in your research (Actors, Incidents, etc.). -
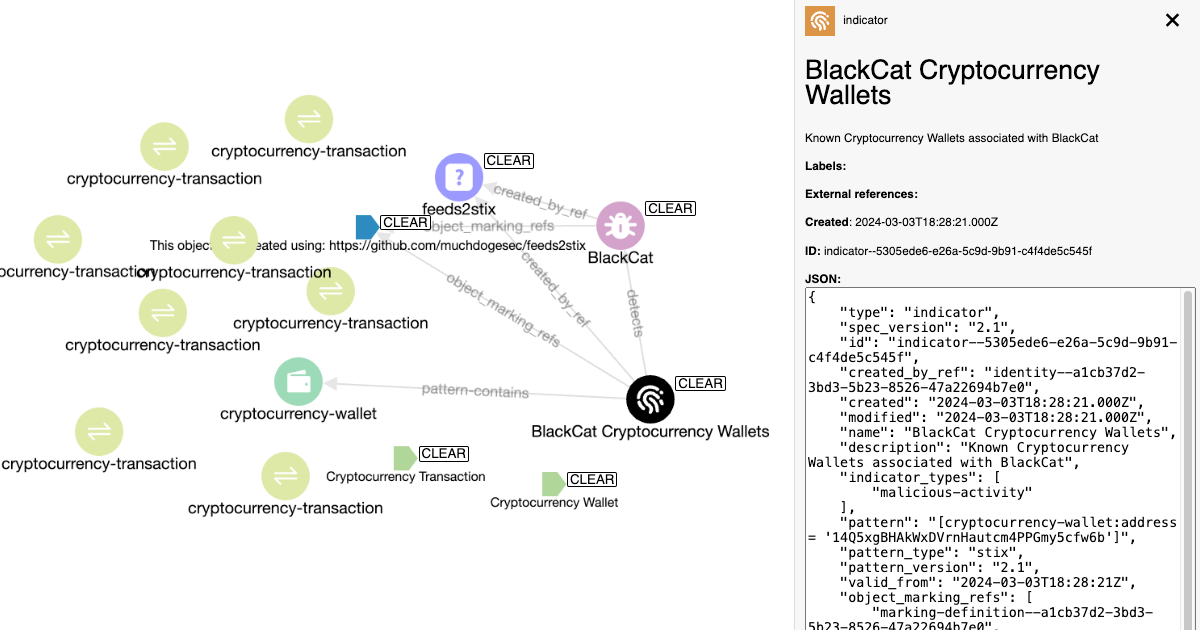
Graphing the Ransomware Payment Ecosystem using STIX Objects
PRODUCTS July 21, 2024
I recently conducted a project to identify the most prolific ransomware based on the ransom payments being made. Let me walk you through how I did it. -
The Problems with Modelling Countries as STIX Objects (and How to Fix Them)
PRODUCTS July 14, 2024
Take the list of recognised countries and regions. Create STIX objects for them. Make them available to everyone so that the CTI world has a single way of representing them.